The Automated Collection and Enrichment (ACE) platform is a suite of tools for threat hunters to collect data from many endpoints in a network and...
Tag - windows
Wapiti allows you to audit the security of your websites or web applications. It performs “black-box” scans (it does not study the source code) of...
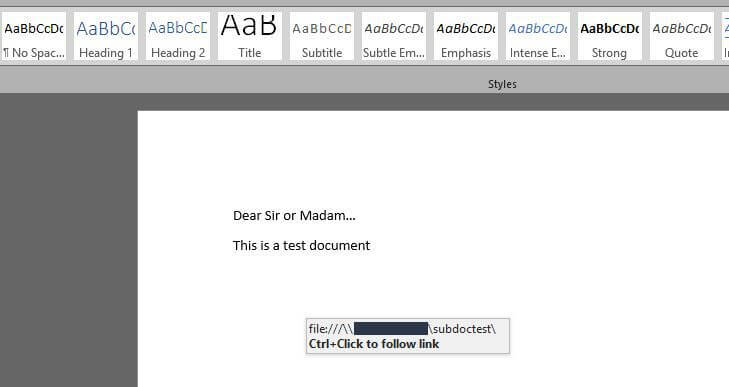
Security researchers from Rhino Labs (a US-based cyber-security firm) have found that cyber criminals can use a Microsoft Word feature dubbed subDoc to fool...
shimit is a python tool that implements the Golden SAML attack. python .\shimit.py -h usage: shimit.py [-h] -pk KEY [-c CERT] [-sp SP] -idp IDP -u USER [-reg...
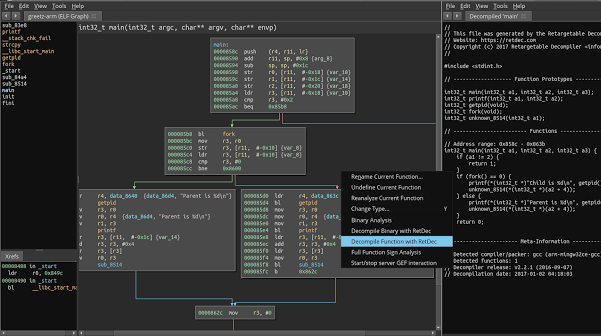
RetDec is a retargetable machine-code decompiler based on LLVM. The decompiler is not limited to any particular target architecture, operating system, or...
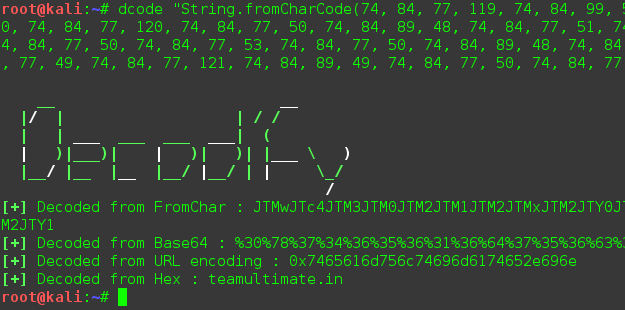
Decodify can detect and decode encoded strings, recursively. Its currently in beta phase. Lets take this string : teamultimate.in and encode it with Hex, URL...
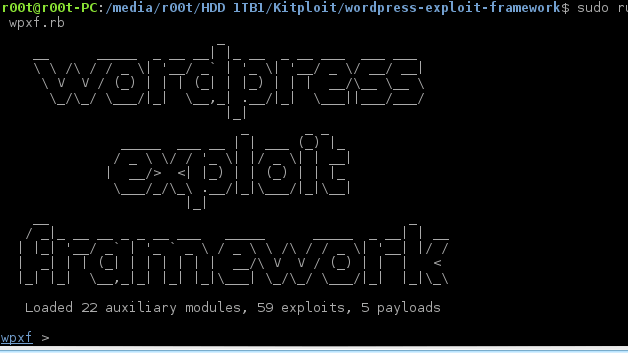
A Ruby framework for developing and using modules which aid in the penetration testing of WordPress powered websites and systems. What do I need to run it...
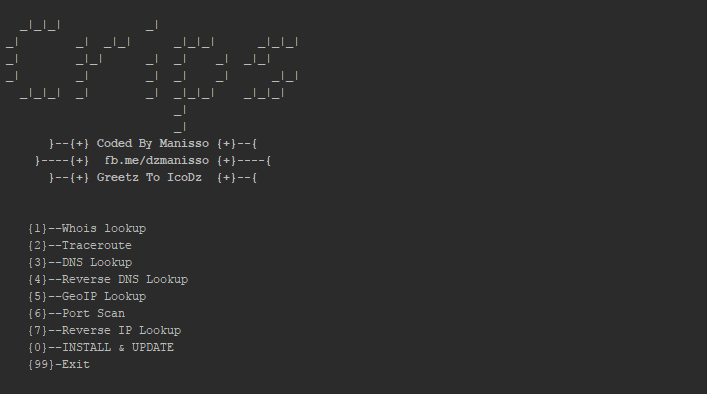
This Tools is a collection of online IP Tools that can be used to quickly get information about IP Address’s, Web Pages and DNS records. Menu Whois...
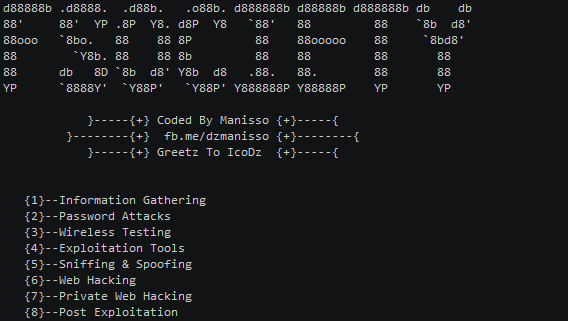
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...
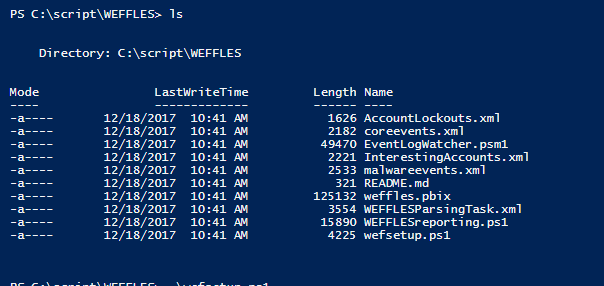
WEFFLES is designed to be small and lightweight, both for speed of getting something deployed during an Incident Response and also for the sake of being...