[sc name=”ad_1″] UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting...
Tag - Vulnerable
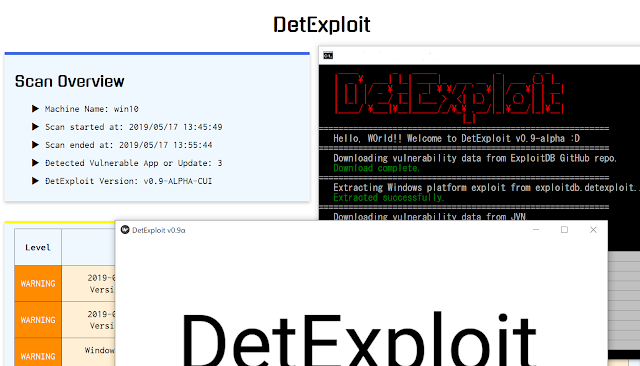
[sc name=”ad_1″] DetExploit is software that detect vulnerable applications and not-installed important OS updates on the system, and notify them...
Manticore is a symbolic execution tool for analysis of binaries and smart contracts. Note: Beginning with version 0.2.0, Python 3.6+ is required. Features...
novahot is a webshell framework for penetration testers. It implements a JSON-based API that can communicate with trojans written in any language. By default...
Advanced search in search engines, enables analysis provided to exploit GET / POST capturing emails & urls, with an internal custom validation junction for...
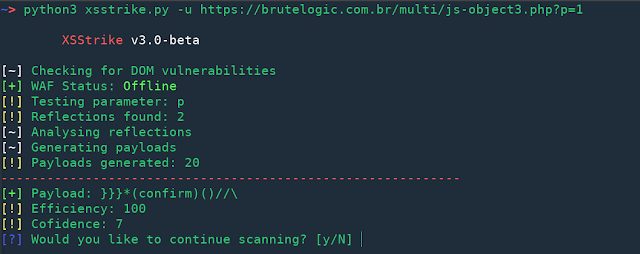
Why XSStrike? Every XSS scanner out there has a list of payloads, they inject the payloads and if the payload is reflected into the webpage, it is declared...
Slither is a Solidity static analysis framework written in Python 3. It runs a suite of vulnerability detectors, prints visual information about contract...
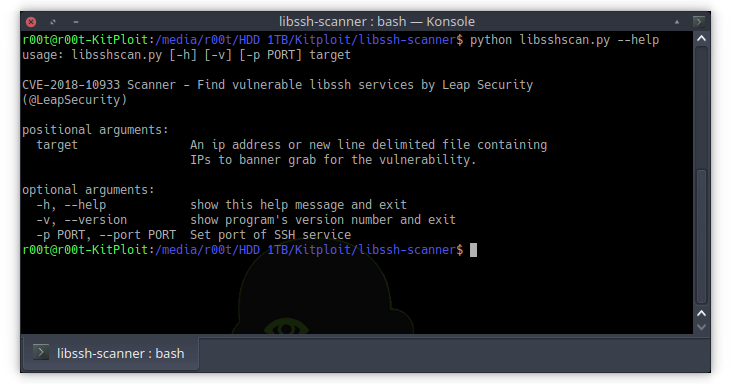
This is a python based script to identify hosts vulnerable to CVE-2018-10933. The vulnerability is present on versions of libssh 0.6+ and was remediated by a...
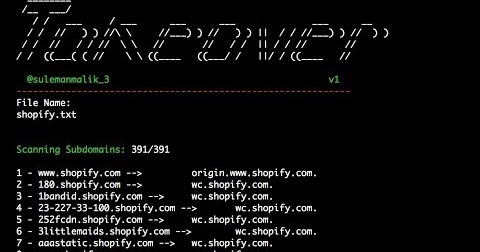
What is Subdomain Takeover? Subdomain takeover is a class of vulnerability where subdomain points to an external service that has been deleted. The external...
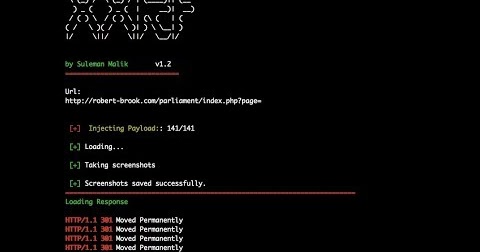
What is SSRF vulnerability? Server Side Request Forgery (SSRF) is a type of vulnerability class where attacker sends crafted request from a vulnerable web...