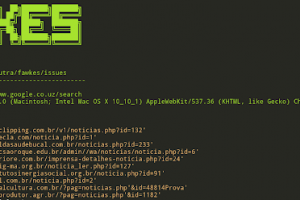
[sc name=”ad_1″] Fawkes is a tool to search for targets vulnerable to SQL Injection. Performs the search using Google search engine. Options...
Tag - Vulnerable
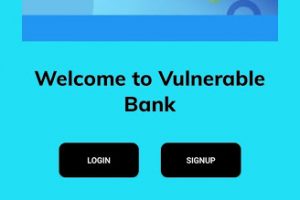
[sc name=”ad_1″] Damn Vulnerable Bank Android Application aims to provide an interface for everyone to get a detailed understanding with internals...
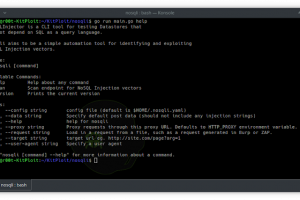
[sc name=”ad_1″] NoSQL scanner and injector. About Nosqli I wanted a better nosql injection tool that was simple to use, fully command line based...
[sc name=”ad_1″] RmiTaste allows security professionals to detect, enumerate, interact and attack RMI services by calling remote methods with...
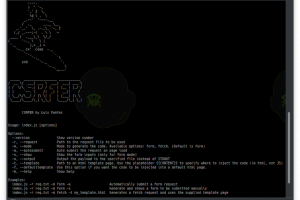
[sc name=”ad_1″] CSRFER is a tool to generate csrf payloads, based on vulnerable requests. It parses supplied requests to generate either a form or...
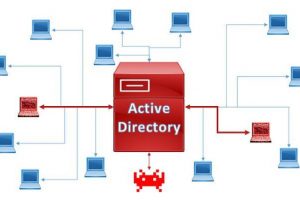
[sc name=”ad_1″] Create a vulnerable active directory that’s allowing you to test most of active directory attacks in local lab. Main...
[sc name=”ad_1″] Some HTTP parameter names are more commonly associated with one functionality than the others. For example, the parameter ?url=...
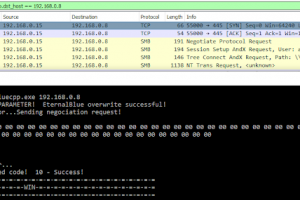
[sc name=”ad_1″] EternalBlue suite remade in C which includes: MS17-010 Exploit, EternalBlue/MS17-010 vulnerability detector, DoublePulsar detector...
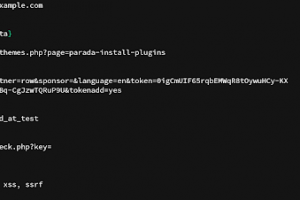
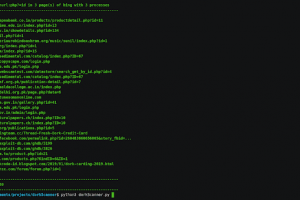
[sc name=”ad_1″] A typical search engine dork scanner that scrapes search engines with queries that you provide in order to find vulnerable URLs...
[sc name=”ad_1″] GoGhost is a High Performance, lightweight, portable Open Source tool for mass SMBGhost Scan. Installation You can download...