[sc name=”ad_1″] This is a proof of concept of how a ransomware works, and some techniques that we usually use to hijack our files. This project is...
Tag - RSA
[sc name=”ad_1″] Why? If you try to learn a little bit more about crypto, either because you want to know how the attacks work or just because you...
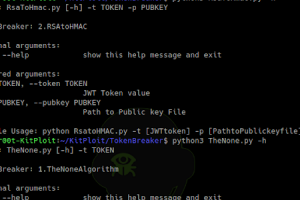
[sc name=”ad_1″] Token Breaker is focused on 2 particular vulnerability related to JWT tokens. None Algorithm RSAtoHMAC Refer to this link about...