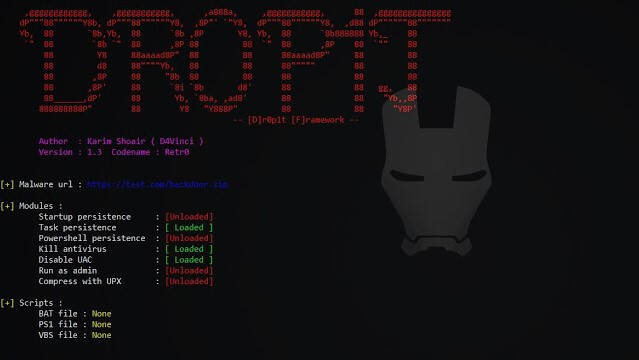
Have you ever heard about trojan droppers ? In short dropper is type of malware that downloads other malwares and Dr0p1t gives you the chance to create a...
Tag - PowerShell
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
Excalibur is an Eternalblue exploit based “Powershell” for the Bashbunny project. It’s purpose is to reflect on how a “simple”...
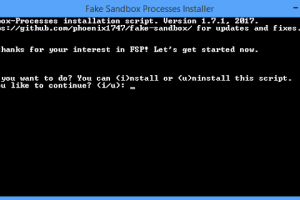
This small script will simulate fake processes of analysis, sandbox and/or VM software that some malware will try to avoid. You can download the original...
Nishang is an open source framework and collection of powerful PowerShell scripts and payloads that you can use during penetration testing audit, post...
TrevorC2 is a client/server model for masking command and control through a normally browsable website. Detection becomes much harder as time intervals are...
ACLight is a tool for discovering privileged accounts through advanced ACLs (Access Lists) analysis. It includes the discovery of Shadow Admins in the scanned...
DET (is provided AS IS), is a proof of concept to perform Data Exfiltration using either single or multiple channel(s) at the same time. This is a Proof of...
WINspect is part of a larger project for auditing different areas of Windows environments. It focuses on enumerating different parts of a Windows machine...
Run PowerShell with dlls only. Does not require access to powershell.exe as it uses powershell automation dlls. dll mode: Usage: rundll32 PowerShdll,main...