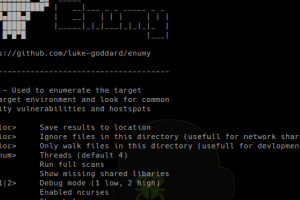
[sc name=”ad_1″] Enumy is portable executable that you drop on target Linux machine during a pentest or CTF in the post exploitation phase. Running...
Tag - post
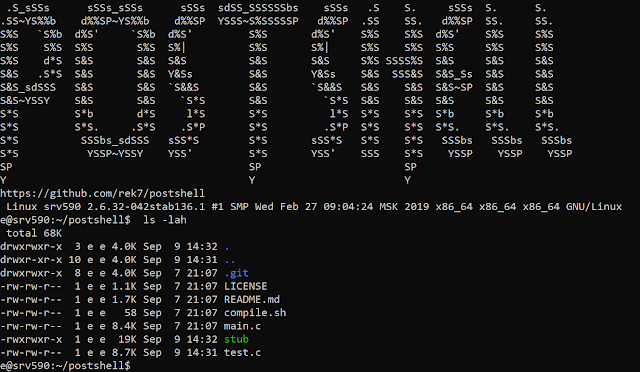
[sc name=”ad_1″] PostShell is a post-exploitation shell that includes both a bind and a back connect shell. It creates a fully interactive TTY...
Wapiti allows you to audit the security of your websites or web applications. It performs “black-box” scans (it does not study the source code) of...
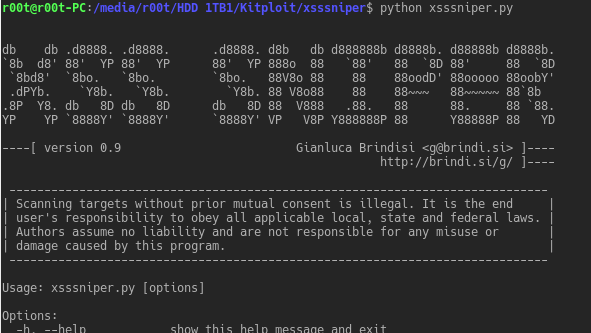
xsssniper is an handy xss discovery tool with mass scanning functionalities. Usage: Usage: xsssniper.py [options] Options: -h, --help show this help message...
XSSSNIPER is an handy xss discovery tool with mass scanning functionalities. Usage: Usage: xsssniper.py [options] Options: -h, --help show this help message...
TrevorC2 is a client/server model for masking command and control through a normally browsable website. Detection becomes much harder as time intervals are...