[sc name=”ad_1″] Web Application Security Recon Automation Framework It takes user input as a domain name and maximize the attack surface area by...
Tag - parameter
[sc name=”ad_1″] Some HTTP parameter names are more commonly associated with one functionality than the others. For example, the parameter ?url=...
[sc name=”ad_1″] RMIScout performs wordlist and bruteforce attacks against exposed Java RMI interfaces to safely guess method signatures without...
[sc name=”ad_1″] Finder Of XSS, and Dal is the Korean pronunciation of moon. What is DalFox Just, XSS Scanning and Parameter Analysis tool. I...
[sc name=”ad_1″] Dolos Cloak is a python script designed to help network penetration testers and red teamers bypass 802.1x solutions by using an...
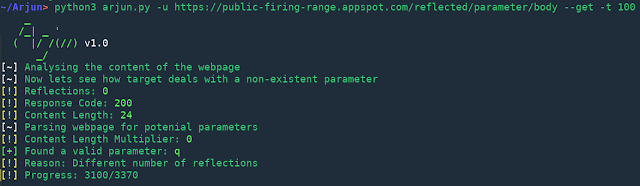
Features Multi-threading 3 modes of detection Regex powered heuristic scanning Huge list of 3370 parameter names Usage Note: Arjun doesn’t work with...
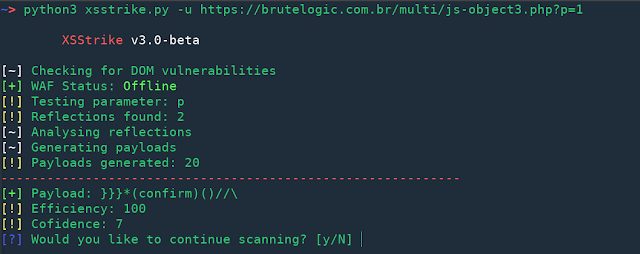
Why XSStrike? Every XSS scanner out there has a list of payloads, they inject the payloads and if the payload is reflected into the webpage, it is declared...
TLS-Scanner is a tool created by the Chair for Network and Data Security from the Ruhr-University Bochum to assist pentesters and security researchers in the...
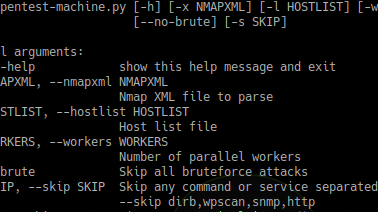
Automates some pentesting work via an nmap XML file. As soon as each command finishes it writes its output to the terminal and the files in output-by-service/...
What is SSRF vulnerability? Server Side Request Forgery (SSRF) is a type of vulnerability class where attacker sends crafted request from a vulnerable web...