What if I told you that there is a method will let you execute commands on Microsoft Word without any Macros, or memory corruption?! This Macro-less code...
Tag - Malware
Rather than heavily protecting backdoors with hardcore packers, many malware authors evade heuristic detections by obfuscating only key portions of an...
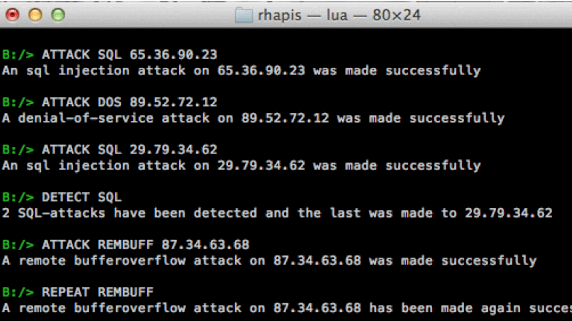
Network intrusion detection systems simulator. RHAPIS provides a simulation environment through which user is able to execute any IDS operation. Basic Usage...
It seems sophisticated hackers have changed the way they conduct targeted cyber operations—instead of investing in zero-days and developing their malware; some...