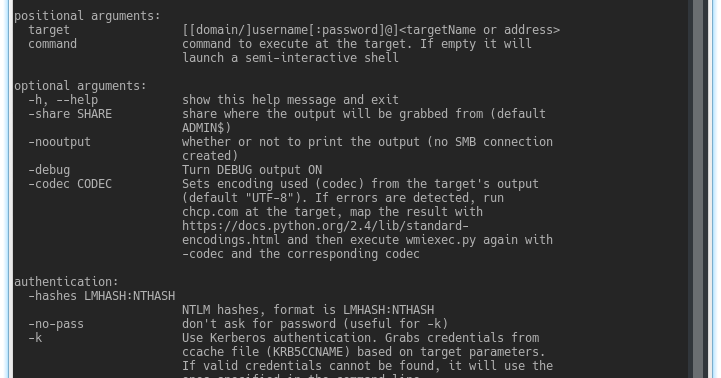
Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets...
Tag - mac
Hash Buster is a program which uses several APIs to perform hash lookups. Features Automatic hash type identification Supports MD5, SHA1, SHA2 Can extract...
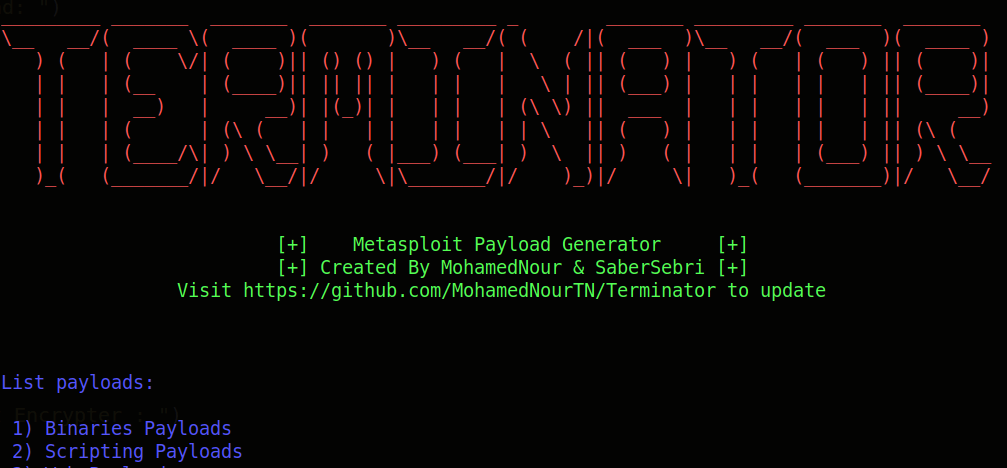
Terminator Metasploit Payload Generator. Payload List : Binaries Payloads 1) Android 2) Windows 3) Linux 4) Mac OS Scripting Payloads 1) Python 2) Perl 3) Bash...
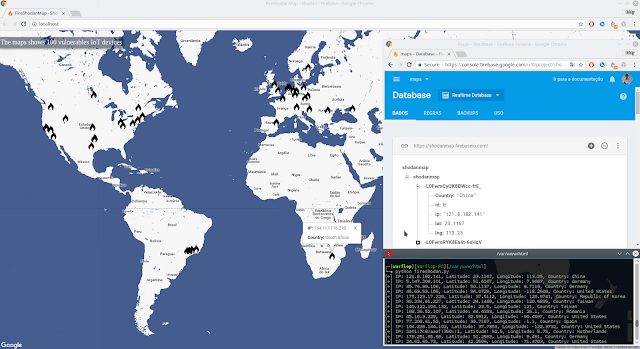
FireShodanMap is a Realtime map that integrates Firebase and Shodan. A search is carried out using Shodan searching vulnerable devices and they are showed on...
p0wnedShell is an offensive PowerShell host application written in C# that does not rely on powershell.exe but runs powershell commands and functions within a...
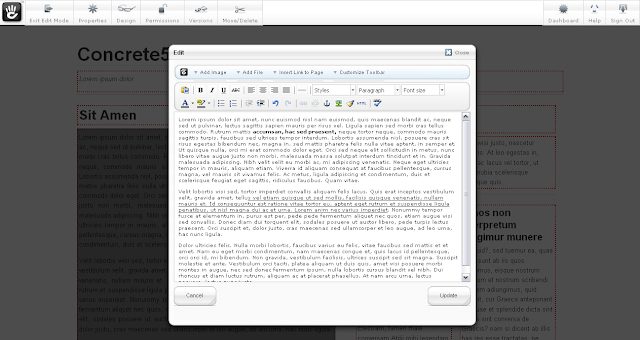
Vulnerability scanner and information gatherer for the Concrete5 CMS. Is a little out of date presently pending a refactor. concrete5 is an open-source content...
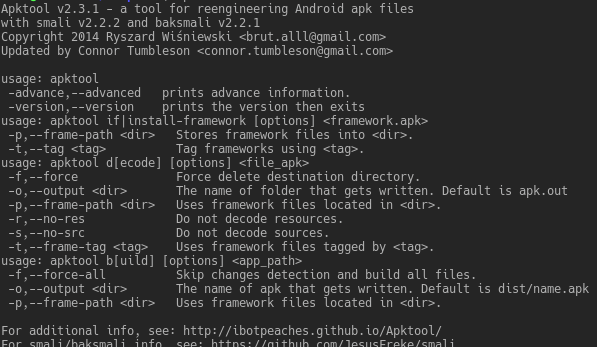
A tool for reverse engineering 3rd party, closed, binary Android apps. It can decode resources to nearly original form and rebuild them after making some...
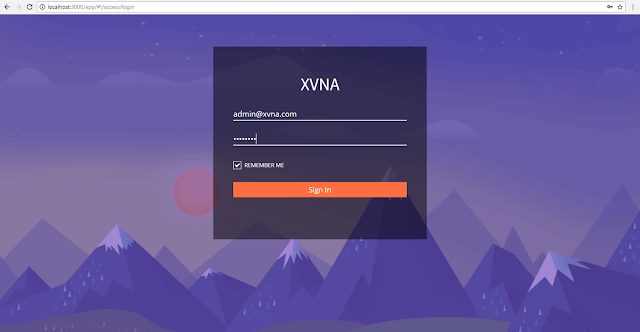
XVNA is an extreme vulnerable node application coded in Nodejs(Expressjs)/MongoDB that helps security enthusiasts to learn application security. it’s not...
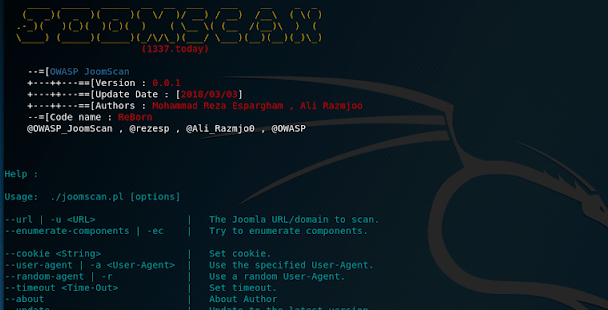
OWASP JoomScan (short for [Joom]la Vulnerability [Scan]ner) is an opensource project in perl programming language to detect Joomla...
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also...