Security researchers have discovered a new privilege-escalation vulnerability in Linux kernel that could allow a local attacker to execute code on the affected...
Tag - linux
About Getting default credentials added to commercial scanners is often difficult and slow. changeme is designed to be simple to add new credentials without...
DET (is provided AS IS), is a proof of concept to perform Data Exfiltration using either single or multiple channel(s) at the same time. This is a Proof of...
Belati is tool for Collecting Public Data & Public Document from Website and other service for OSINT purpose. This tools is inspired by Foca and Datasploit...
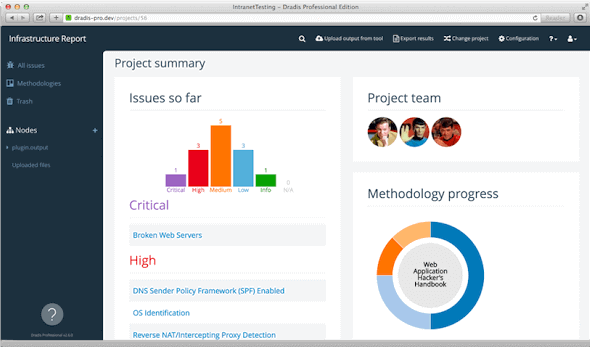
Dradis is an open-source collaboration framework, tailored to InfoSec teams. Goals Share the information effectively. Easy to use, easy to be adopted...
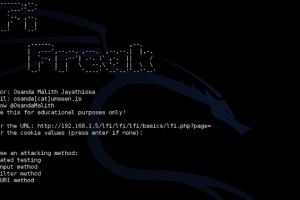
LFiFreak is a tool for exploiting local file inclusions using PHP Input, PHP Filter and Data URI methods. Features Works with Windows, Linux and OS X Includes...
Tails is a live system that aims to preserve your privacy and anonymity. It helps you to use the Internet anonymously and circumvent censorship almost anywhere...
Hey Guys, In this video i show you how to generate shellcodes and Backdoors using ShellSploit Framework and Kali Linux 2017.2. ShellSploit: Shellsploit...
Hey Guys, In this video i show you a great Security Auditing Tool for Unix/Linux Systems called Lynis. Lynis is an open source security auditing tool. Used by...
Sniffer is a C program that parses and interprets captured Ethernet traffic containing IP datagrams (UDP/TCP), and stores the captured payloads, email messages...