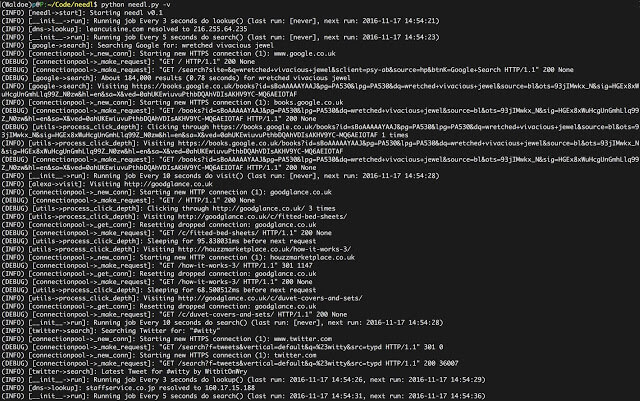
Take back your privacy. Lose yourself in the haystack. Your ISP is most likely tracking your browsing habits and selling them to marketing agencies (albeit...
Tag - linux
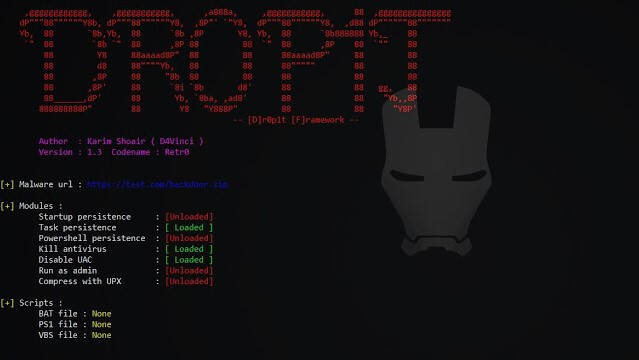
Have you ever heard about trojan droppers ? In short dropper is type of malware that downloads other malwares and Dr0p1t gives you the chance to create a...
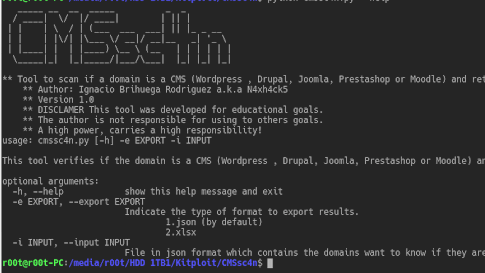
Tool to identify if a domain is a CMS such as WordPress, Moodle, Joomla, Drupal or Prestashop. Use python cmssc4n.py -h _____ __ __ _____ _ _ / ____| \/ |/...
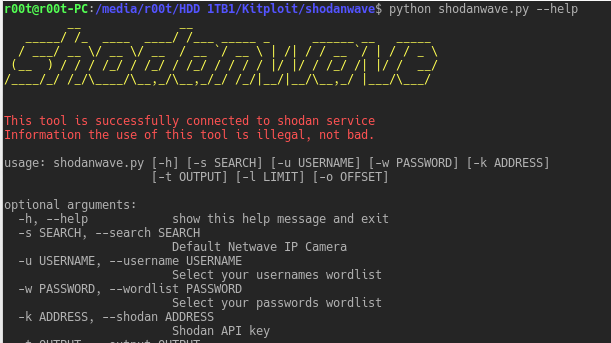
Shodanwave is a tool for exploring and obtaining information from cameras specifically Netwave IP Camera. The tool uses a search engine called shodan that...
Some work has been already published regarding the subject of cryptograhic keys security within DRAM. Basically, we need to find something that looks like a...
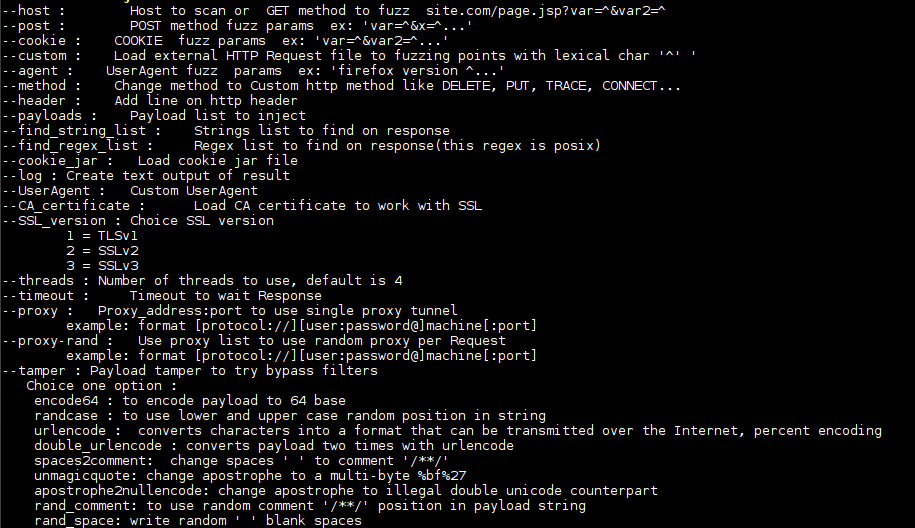
Web security tool to make fuzzing at HTTP inputs, made in C with libCurl. 0d1n is a tool for automating customized attacks against web applications. You can...
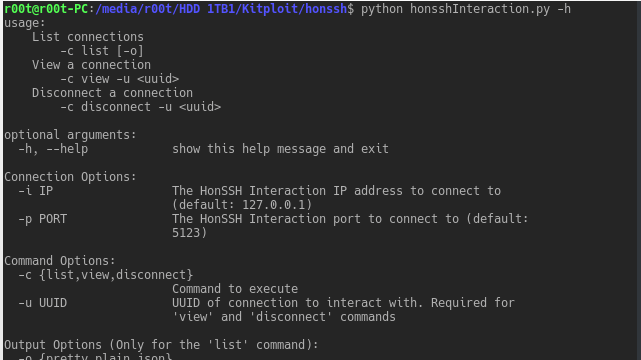
HonSSH is a high-interaction Honey Pot solution. HonSSH will sit between an attacker and a honey pot, creating two separate SSH connections between them...
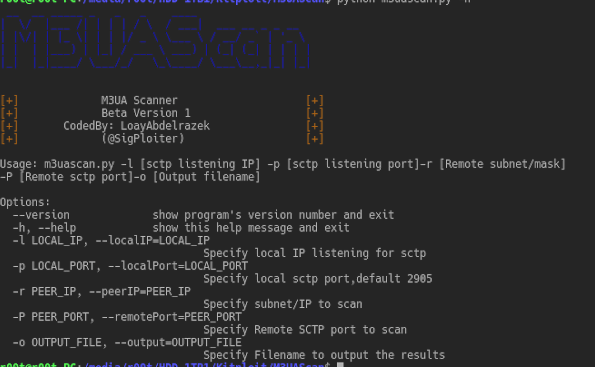
A Scanner for M3UA protocol to detect Sigtran supporting nodes M3UA stands for MTP Level 3 (MTP3) User Adaptation Layer as defined by the IETF SIGTRAN working...
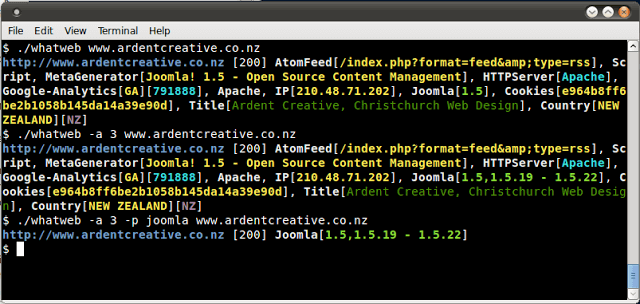
WhatWeb identifies websites. Its goal is to answer the question, “What is that Website?”. WhatWeb recognises web technologies including content management...
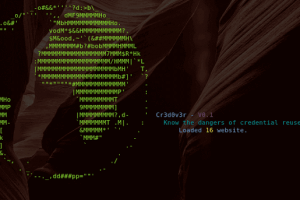
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...