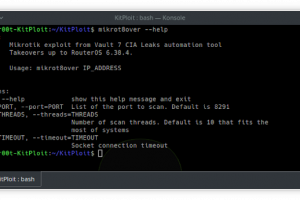
[sc name=”ad_1″] mikrot8over: Fast exploitation tool for Mikrotik RouterOS up to 6.38.4 This is reworked original Mikrotik Exploit. Added Python 2...
Tag - leaks
[sc name=”ad_1″] Enumerate valid usernames from Office 365 using ActiveSync, Autodiscover, or office.com login page. Usage o365enum will read...
[sc name=”ad_1″] PwnedPasswordsChecker is a tool that checks if the hash of a known password (in SHA1 or NTLM format) is present in the list of I...
[sc name=”ad_1″] A Proof-of-Concept bind shell using the Fax service and a DLL hijack based on Ualapi.dll. See our writeup at: How to use Build...
LeakScraper is an efficient set of tools to process and visualize huge text files containing credentials. These tools are designed to help...
GlobaLeaks is an open-source, free software intended to enable secure and anonymous whistleblowing initiatives developed by the Hermes Center for Transparency...
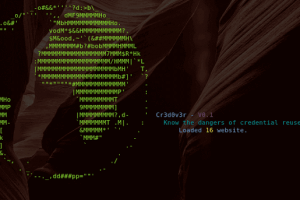
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...
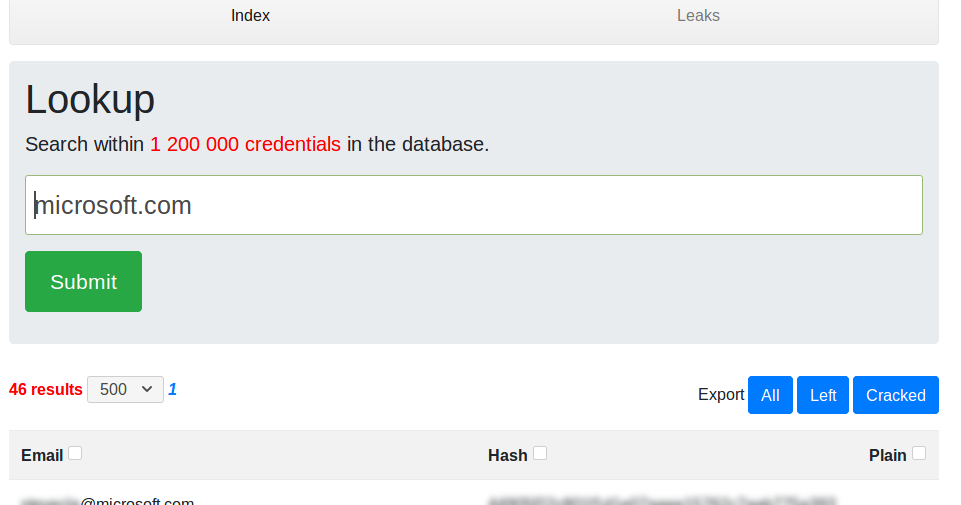
A Tool To Help You Manage Your Leaks Install sudo apt-get install mongodb-org screen pip3 install -r requeriments.txt Usage screen -S leakManager hug -f index...