[sc name=”ad_1″] Every app installed on your smartphone with permission to access location service “can” continually collect your real...
Tag - how to hack
[sc name=”ad_1″] A team of cybersecurity researchers from the University of New Haven yesterday released a video demonstrating how vulnerabilities...
[sc name=”ad_1″] Developers of Drupal—a popular open-source content management system software that powers millions of websites—have released the...
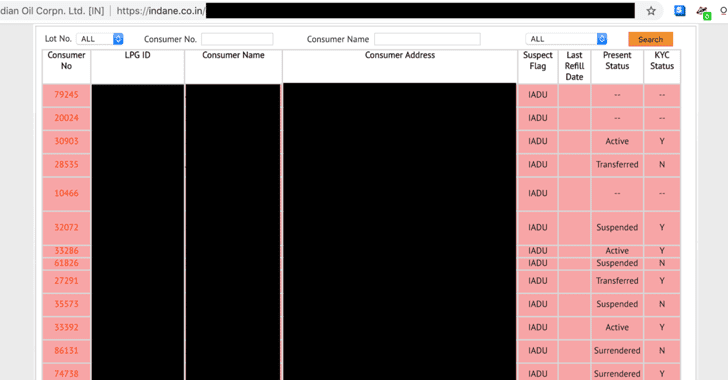
[sc name=”ad_1″] Exclusive — A security researcher has identified an unsecured server that was leaking detailed personal details of nearly half a...
[sc name=”ad_1″] Beware Windows users… a new dangerous remote code execution vulnerability has been discovered in the WinRAR software...
[sc name=”ad_1″] Exclusive — If you have not updated your website to the latest WordPress version 5.0.3, it’s a brilliant idea to upgrade the...
[sc name=”ad_1″] How do you know whether an attacker has infiltrated your network? Can you really rely on an Endpoint Detection and Response (EDR)...
[sc name=”ad_1″] Why would someone bother to hack a so-called “ultra-secure encrypted database that is being protected behind 13 feet high...
[sc name=”ad_1″] It’s 2019, and just clicking on a specially crafted URL would have allowed an attacker to hack your Facebook account without...
[sc name=”ad_1″] Wohooo! Great news for hackers and penetration testers. Offensive Security has just released Kali Linux 2019.1, the first 2019...