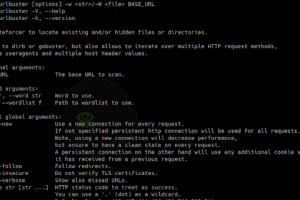
[sc name=”ad_1″] Powerful web directory fuzzer to locate existing and/or hidden files or directories. Similar to dirb or gobuster, but with a lot...
Tag - hidden
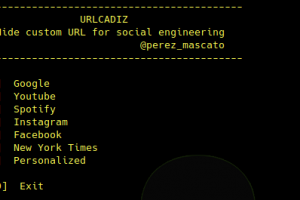
[sc name=”ad_1″] A simple script to generate a hidden url for social engineering. Legal disclaimer: Usage of URLCADIZ for attacking targets without...
[sc name=”ad_1″] FOCA (Fingerprinting Organizations with Collected Archives) FOCA is a tool used mainly to find metadata and hidden information in...
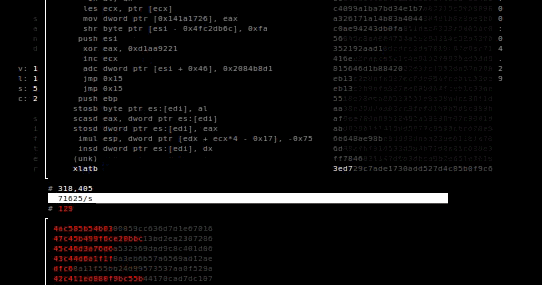
The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s...
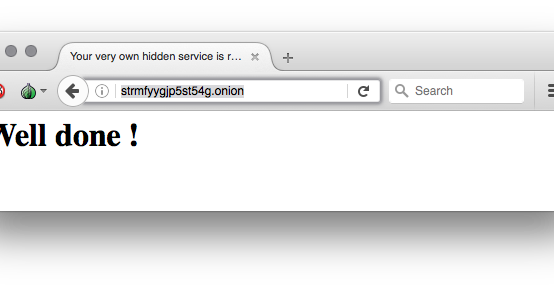
Easily run a hidden service inside the Tor network with this container Generate the skeleton configuration for you hidden service, replace for your hidden...
pspy is a command line tool designed to snoop on processes without need for root permissions. It allows you to see commands run by other users, cron jobs, etc...
This project is a Docker image useful for solving Steganography challenges as those you can find at CTF platforms like hackthebox.eu. The image comes...
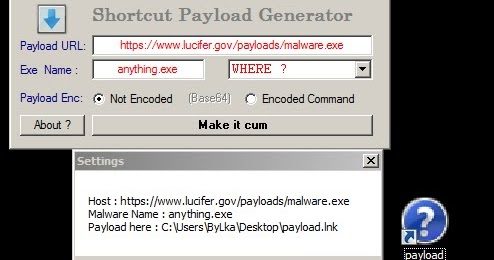
Making FUD Shortcut (.lnk) payloads with LNK-KISSER to remote execute malicious code. Shortcut-Payload-Generator Exploiting Powershell to make ShortCut...
The goal of this volatility plugin is to extract a screenshot of all open X windows from a memory dump. Overview The plugin first dumps the X server memory...