A framework based on the Fiddler web debugger to study Exploit Kits, malvertising and malicious traffic in general. Installation Download and install the...
Tag - Exploit
Often during the penetration test engagement the security analyst faces the problem of identifying privilege escalation attack vectors on tested Linux...
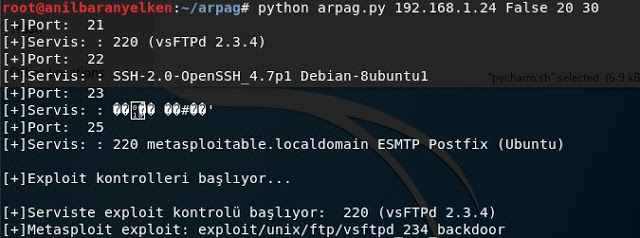
arpa?: In Turkish mythology magical word means. The tool name arpag has been selected because it has made the exploit process automatic. Installation: git...
Shodan is a search engine that lets the user find specific types of computers (webcams, routers, servers, etc.) connected to the internet using a variety of...
As the name might suggest AutoSploit attempts to automate the exploitation of remote hosts. Targets are collected automatically as well by employing the Shodan...
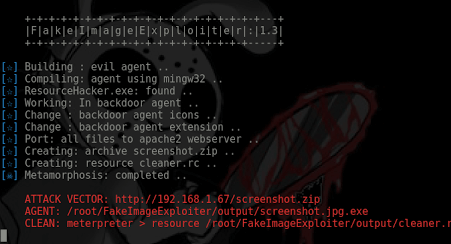
This module takes one existing image.jpg and one payload.ps1 (input by user) and builds a new payload (agent.jpg.exe) that if executed it will trigger the...
Speculative optimizations execute code in a non-secure manner leaving data traces in microarchitecture such as cache. Refer to the paper by Lipp et. al 2017...
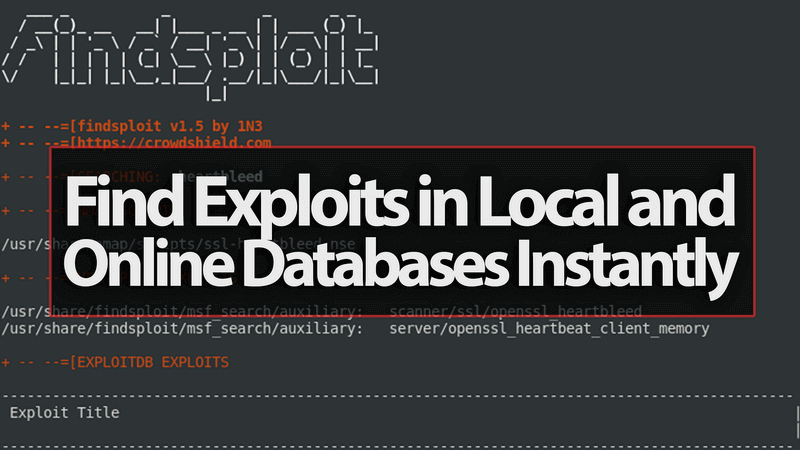
Findsploit is a simple bash script to quickly and easily search both local and online exploit databases. Findsploit: Installation: git clone cd Findsploit...
Google’s Project Zero iOS bug hunter Ian Beer has released details about an iOS 11 exploit that could offer up a jailbreak for iOS 11.1.2. Beer last week...
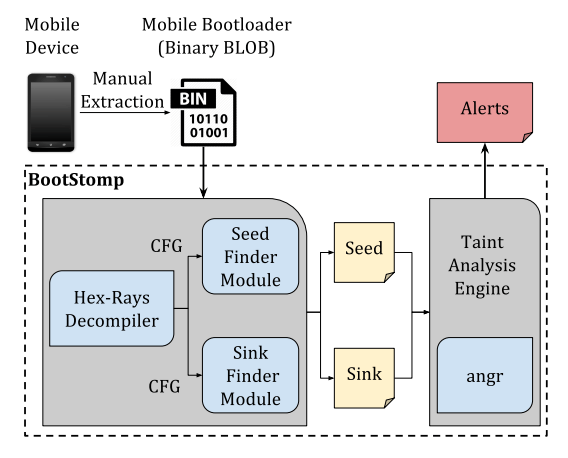
BootStomp is a boot-loader bug finder. It looks for two different class of bugs: memory corruption and state storage vulnerabilities. For more info please...