[sc name=”ad_1″] Tested environments: Windows, MAC, linux, and windows subsystem for linux (WSL) What can SourceWolf do? Crawl through responses to...
Tag - Code
[sc name=”ad_1″] Be sure to change the ftp variables throughout the code, these variables contain the username, password, & IP address of the...
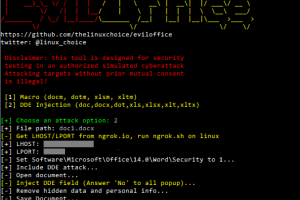
[sc name=”ad_1″] Win python script to inject Macro and DDE code into Excel and Word documents (reverse shell) Features: Inject malicious Macro on...
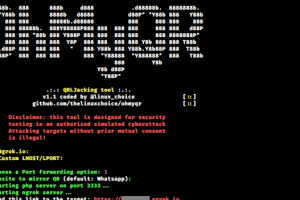
[sc name=”ad_1″] QRLJacking or Quick Response Code Login Jacking is a simple social engineering attack vector capable of session hijacking...
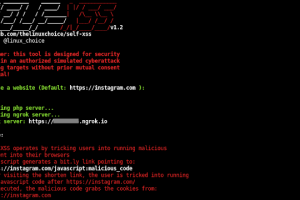
[sc name=”ad_1″] Self-XSS attack using bit.ly to grab cookies tricking users into running malicious code How it works? Self-XSS is a social...
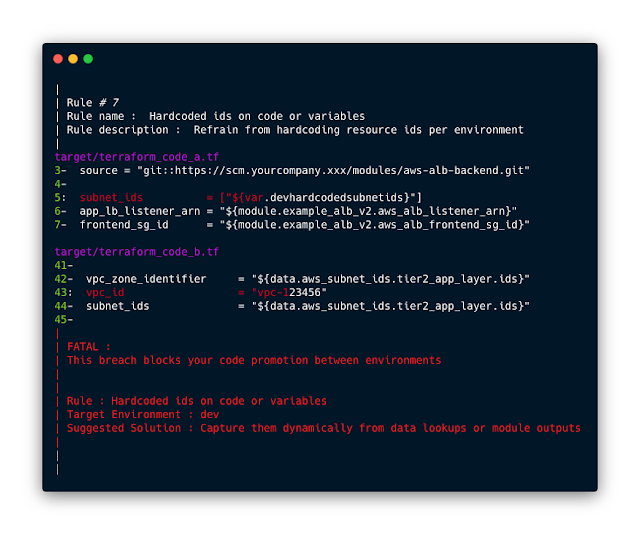
[sc name=”ad_1″] Stupidly easy to use, small footprint Policy as Code subsecond command-line scanner that leverages the power of the fastest multi...
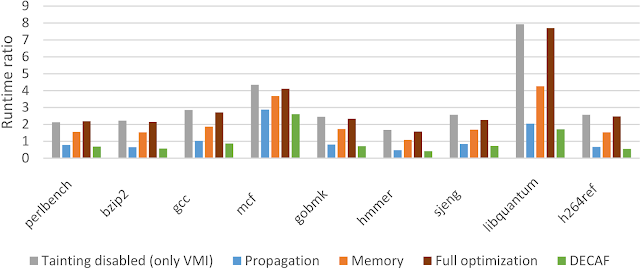
[sc name=”ad_1″] DECAF++, the new version of DECAF, taint analysis is around 2X faster making it the fastest, to the best of our knowledge, whole...
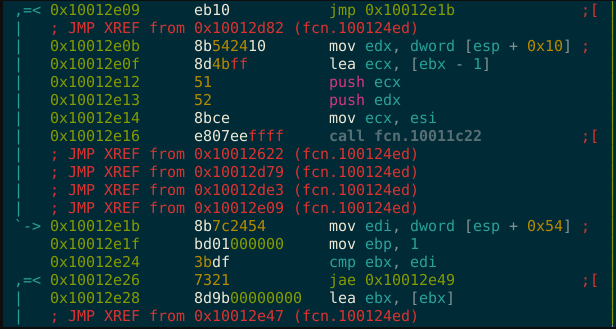
[sc name=”ad_1″] metame is a simple metamorphic code engine for arbitrary executables. From Wikipedia: Metamorphic code is code that when run...
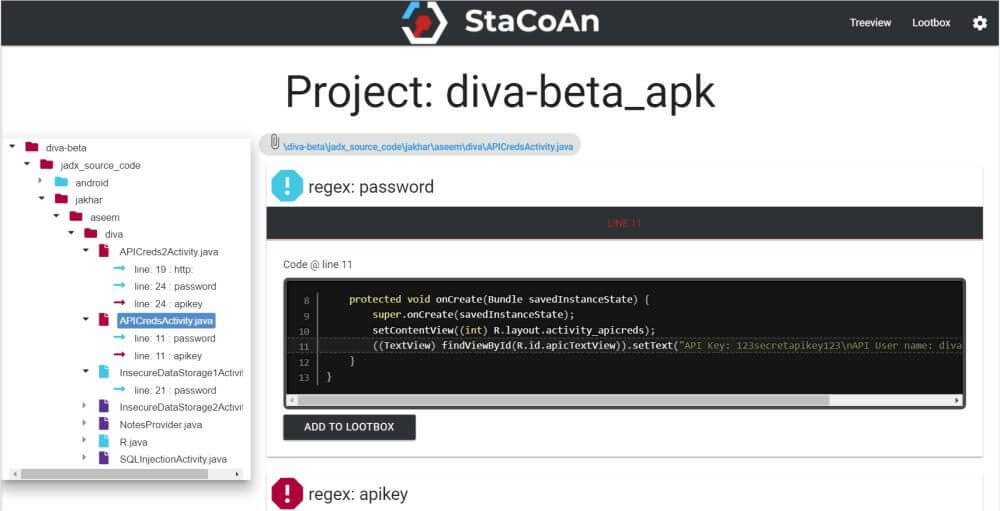
StaCoAn is a crossplatform tool which aids developers, bugbounty hunters and ethical hackers performing static code analysis on mobile applications. This tool...
WPSploit is intended for Penetration Testers who audit WordPress plugins or developers who wish to audit their own WordPress plugins. It checks for: Cross-Site...