[sc name=”ad_1″] WordPress user enumeration and login Brute Force tool for Windows and Linux With the Brute Force tool, you can control how...
Tag - Brute-force
[sc name=”ad_1″] 0d1n is a tool for automating customized attacks against web applications. This tool is very faster because uses thread pool and C...
[sc name=”ad_1″] enum4linux-ng.py is a rewrite of Mark Lowe’s (former Portcullis Labs now Cisco CX Security Labs) enum4linux.pl, a tool for...
[sc name=”ad_1″] Linux evil toolkit is a framework that aims to centralize, standardize and simplify the use of various security tools for pentest...
[sc name=”ad_1″] RmiTaste allows security professionals to detect, enumerate, interact and attack RMI services by calling remote methods with...
[sc name=”ad_1″] h2cSmuggler smuggles HTTP traffic past insecure edge-server proxy_pass configurations by establishing HTTP/2 cleartext (h2c)...
[sc name=”ad_1″] A set of scripts to help perform an online dictionary attack against a WPA3 access point. Wacker leverages the wpa_supplicant...
[sc name=”ad_1″] h4rpy is an automated WPA/WPA2 PSK attack tool, wrapper of aircrack-ng framework. h4rpy provides clean interface for automated...
[sc name=”ad_1″] Tested environments: Windows, MAC, linux, and windows subsystem for linux (WSL) What can SourceWolf do? Crawl through responses to...
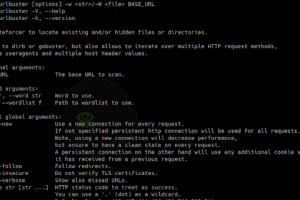
[sc name=”ad_1″] Powerful web directory fuzzer to locate existing and/or hidden files or directories. Similar to dirb or gobuster, but with a lot...