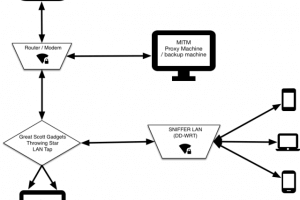
Essentially it’s a WiFi hotspot that is continually collecting all the packets transmitted across it. All connected clients’ HTTPS communications are subjected...
Tag - Attack
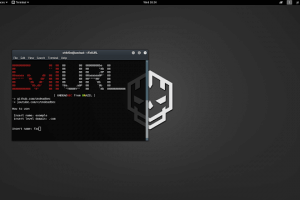
An unicode domain phishing generator for IDN Homograph Attack. CLONE git clone RUNNING cd EvilURL python evilurl.py PREREQUISITES python 2.7 TESTED ON Kali...
Striker is an offensive information and vulnerability scanner. Features Just supply a domain name to Striker and it will automatically do the following for...
Wesley Neelen (security researcher) has received a phishing email that seems to be from the legal online Ethereum wallet site Myetherwallet.com. Cybercriminals...
DUHK (Don’t Use Hard-coded Keys) is a new crypto implementation attack that could enable attackers to obtain secret keys that secure VPN (Virtual Private...
Not the first news of this nature but it was very recently discovered that Microsoft suffered a cyber attack from a group of very intelligent hackers way back...
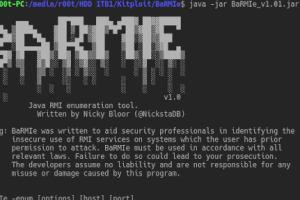
BaRMIe is a tool for enumerating and attacking Java RMI (Remote Method Invocation) services. RMI services often expose dangerous functionality without adequate...
BaRMIe is a tool for enumerating and attacking Java RMI (Remote Method Invocation) services. RMI services often expose dangerous functionality without adequate...