v3n0m is a free and open source scanner. Evolved from baltazar’s scanner, it has adapted several new features that improve functionality and usability. It is...
Search Results For - vulnerabilities
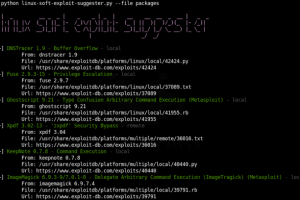
linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages...
This scam email is nearly well designed. The scammers are using a template system to create individualized reports with specific recipient data. This works...
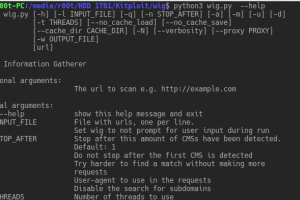
wig is a web application information gathering tool, which can identify numerous Content Management Systems and other administrative applications. The...
Network Security Monitoring (NSM) is, put simply, monitoring your network for security related events. It might be proactive, when used to identify...
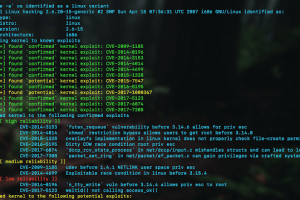
kernelpop is a framework for performing automated kernel exploit enumeration on Linux, Mac, and Windows hosts. Requirements python3 Currently supported...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
News reported in June that McAfee was amongst several Western technology organizations that had acceded in recent years to larger demands by Moscow for access...
The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools and is actively maintained by hundreds of international volunteers*. It...
Just a year after Mirai—biggest IoT-based malware that caused vast Internet outages by launching massive DDoS attacks—completed its first anniversary, security...