Apple uses the Tenth Anniversary iPhone X Phone to replace Touch ID. Because the award handset features an edge-to-edge protection and has very slim bezels...
Search Results For - scanner
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next...
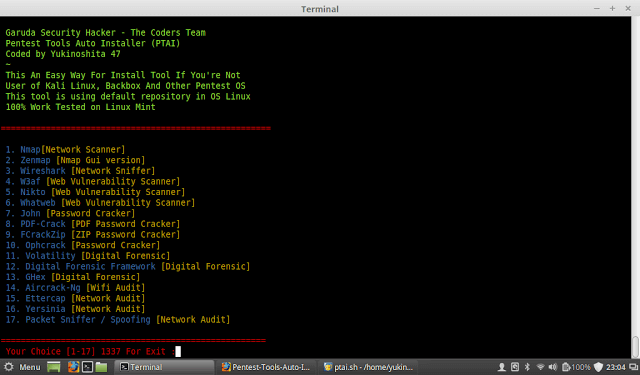
A Simple tool for installing pentest tools and forensic tools on Debian / Ubuntu Based OS Tested on Linux Mint And Kali Linux How To Do ?? Change Your...
Reptile is a LKM rootkit for evil purposes. If you are searching stuff only for study purposes, see the demonstration codes. Features Give root to unprivileged...
Seccubus automates regular vulnerability scans with various tools and aids security people in the fast analysis of its output, both on the first scan and on...
Blazy is a modern login page bruteforcer. Features Easy target selections Smart form and error detection CSRF and Clickjacking Scanner Cloudflare and WAF...
Intelligence and Reconnaissance Package/Bundle installer. IntRec-Pack is a Bash script designed to download, install and deploy several quality OSINT, Recon...
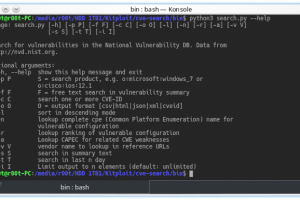
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
It was used in an academic journal paper titled “Novel SIP-based DDoS Attacks and Effective Defense Strategies” published in Computers & Security 63 (2016)...
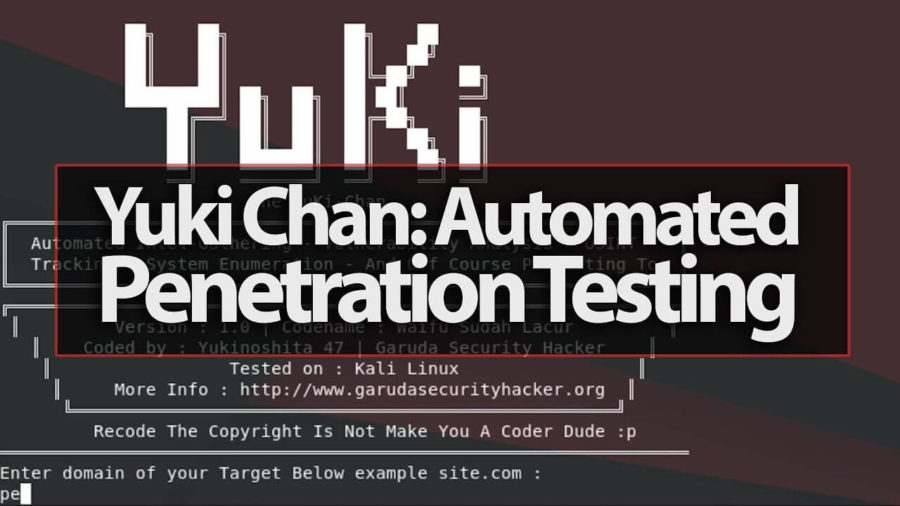
Hey Guys, In this video i show you a great tool called Yuki Chan. The Yuki Chan is an Automated Penetration Testing tool this tool will auditing all standard...