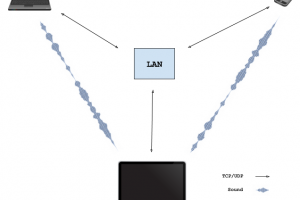
[sc name=”ad_1″] A proof-of-concept for WebRTC signaling using sound. Works with all devices that have microphone + speakers. Runs in the browser...
Search Results For - iOS
[sc name=”ad_1″] A set of scripts to help perform an online dictionary attack against a WPA3 access point. Wacker leverages the wpa_supplicant...
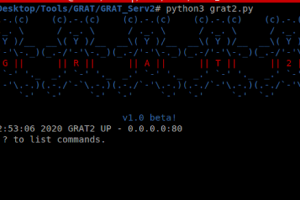
[sc name=”ad_1″] GRAT2 is a Command and Control (C2) tool written in python3 and the client in .NET 4.0. The main idea came from Georgios Koumettou...
[sc name=”ad_1″] C/C++ source obfuscator for antivirus bypass. Build docker build . -t avcleaner docker run -v ~/dev/scrt/avcleaner:/home/toto -it...
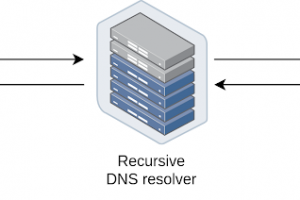
[sc name=”ad_1″] Browsertunnel is a tool for exfiltrating data from the browser using the DNS protocol. It achieves this by abusing dns-prefetch, a...
[sc name=”ad_1″] Bug Bounty Recon (bbrecon) is a free Recon-as-a-Service for bug bounty hunters and security researchers. The API aims to provide a...
[sc name=”ad_1″] A security framework for enterprises and Red Team personnel, supports CobaltStrike’s penetration testing of other...
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
[sc name=”ad_1″] Create a vulnerable active directory that’s allowing you to test most of active directory attacks in local lab. Main...
[sc name=”ad_1″] Bpytop, bashtop python port is now available at It’s a lot faster and about a third as cpu heavy and has more features...