This Kali release is the first to include the Linux 4.15 kernel, which includes the x86 and x64 fixes for the much-hyped Spectre and Meltdown vulnerabilities...
Search Results For - Wireless
Hey Guys, In this video i show you how to perform Wi-Fi deauthentication attack on any Wi-Fi Network. Wi-Fi deauthentication attack is a type of denial-of...
Raspberry Pi 3 Model B+ is now on sale for $35 (the same price as the existing Raspberry Pi 3 Model B), featuring: A 1.4GHz 64-bit quad-core ARM Cortex-A53 CPU...
MAC Changer is an utility that makes the maniputation of MAC addresses of network interfaces easier. A media access control (Mac) address of a device is a...
Kali Linux 2018.1 the first release of 2018, this fine release contains all updated packages and bug fixes since our 2017.3 release last November. This release...
The group, which embodies countless tech organizations including Google, Amazon, Facebook, Etsy and various companies, stated that the organization will not...
At last, Wi-Fi security — or lack of — is about to get its day in the sun. The Wi-Fi Alliance, an industry body made up of device makers including...
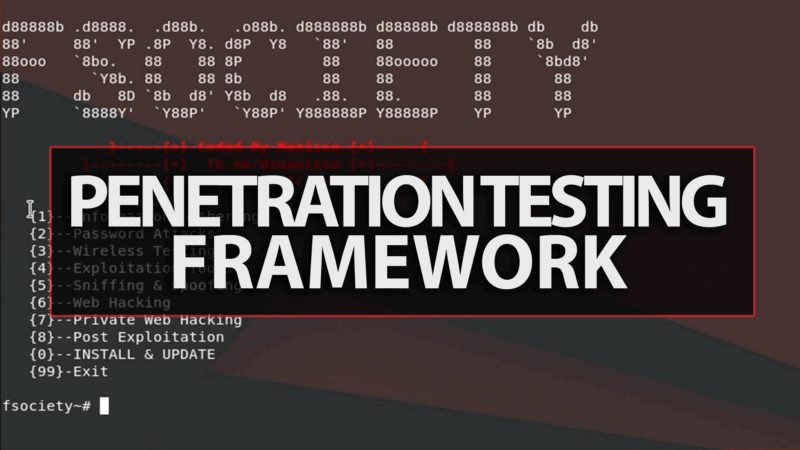
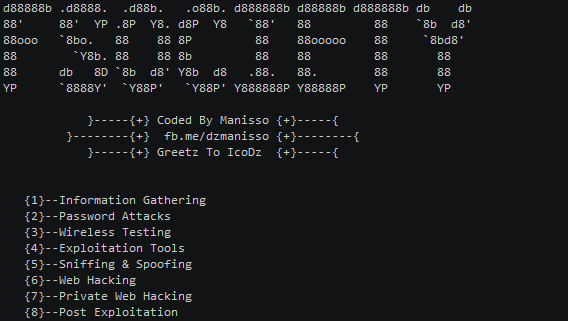
A Penetration Testing Framework, you will have every script that a hacker needs Fsociety: Menu Information Gathering Password Attacks Wireless Testing...
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...
Wifiphisher is a security tool that mounts automated victim-customized phishing attacks against WiFi clients in order to obtain credentials or infect the...