[sc name=”ad_1″] A fast HTTP enumerator that allows you to execute a large number of HTTP requests, filter the responses and display them in real...
Search Results For - Windows
[sc name=”ad_1″] …a simple, self-contained modular host-based IOC scanner Spyre is a simple host-based IOC scanner built around the YARA...
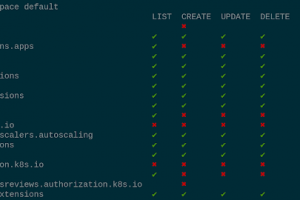
[sc name=”ad_1″] Review Access – kubectl plugin to show an access matrix for server resources Intro Have you ever wondered what access rights...
[sc name=”ad_1″] Pentest Cyber Range for a small Active Directory Domain. Automated templates for building your own Pentest/Red Team/Cyber Range in...
[sc name=”ad_1″] SNIcat is a proof of concept tool that performs data exfiltration, utilizing a covert channel method via. Server Name Indication...
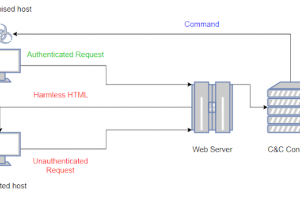
[sc name=”ad_1″] LOLBITS is a C2 framework that uses Microsoft’s Background Intelligent Transfer Service (BITS) to establish the...
[sc name=”ad_1″] A security framework for enterprises and Red Team personnel, supports CobaltStrike’s penetration testing of other...
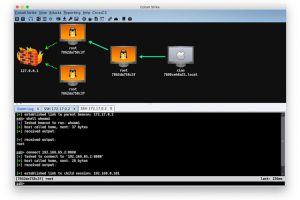
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
[sc name=”ad_1″] Tested environments: Windows, MAC, linux, and windows subsystem for linux (WSL) What can SourceWolf do? Crawl through responses to...
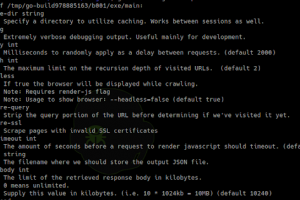
[sc name=”ad_1″] A golang utility to spider through a website searching for additional links with support for JavaScript rendering. Install go get ...