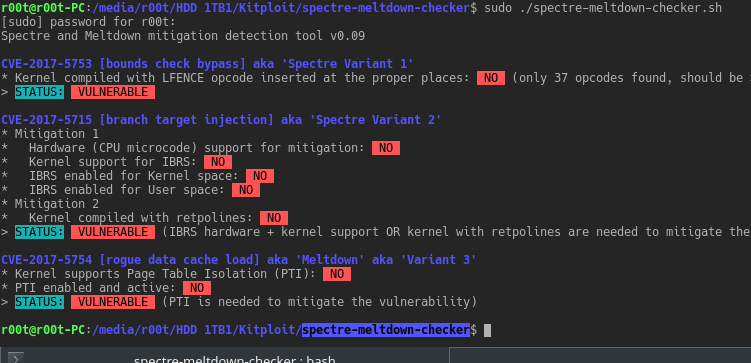
A simple shell script to tell if your Linux installation is vulnerable against the 3 “speculative execution” CVEs: CVE-2017-5753 bounds check...
Search Results For - Vulnerable
Speculative optimizations execute code in a non-secure manner leaving data traces in microarchitecture such as cache. Refer to the paper by Lipp et. al 2017...
The prosecutions were filed in California, Oregon, and Indiana, according to The News. The three incidents focus on the setback in Intel disclosing the...
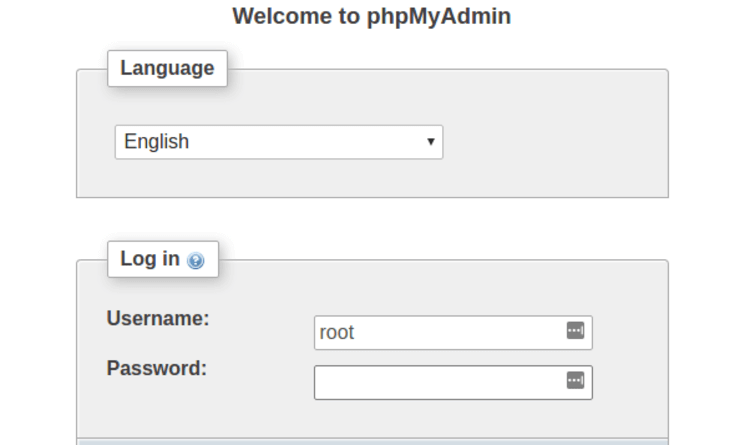
Amongst the most common and in demand applications for MySQL database management is the phpMyAdmin, which became vulnerable, when a critical flaw was found in...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
Recently, Triconex Industries was put at risk when hackers attempted to hack into its security systems, trying to control things. These attacks have a pattern...
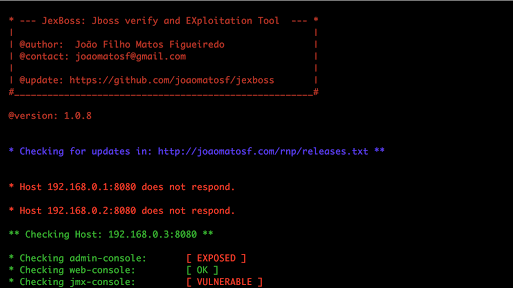
JexBoss is a tool for testing and exploiting vulnerabilities in JBoss Application Server and others Java Platforms, Frameworks, Applications, etc. Requirements...
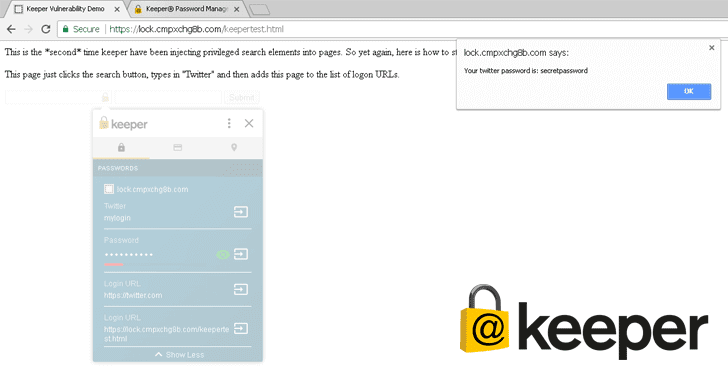
If you are running Windows 10 on your PC, then there are chances that your computer contains a pre-installed 3rd-party password manager app that lets attackers...
Even software that has been built with secure development procedures may still be vulnerable to attack, due to flaws in the interpreted programming languages...
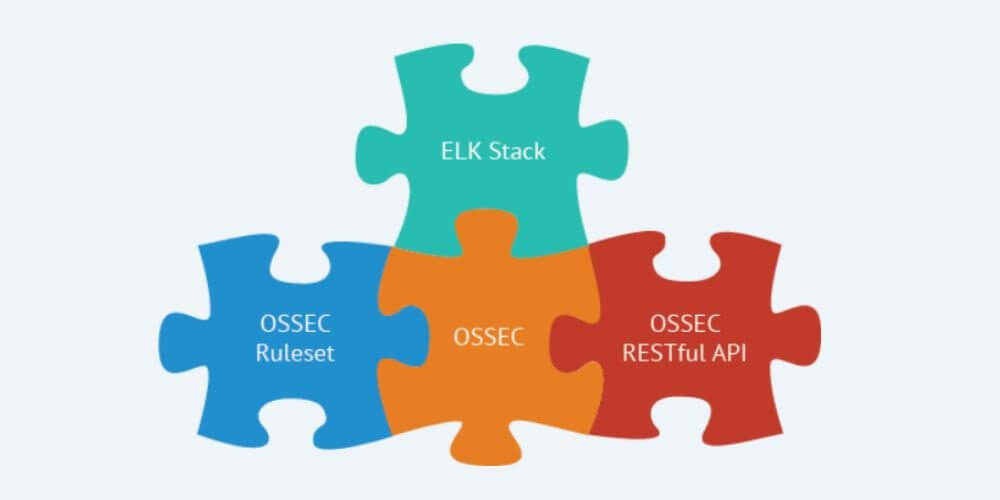
Wazuh is a security detection, visibility, and compliance open source project. It was born as a fork of OSSEC HIDS, later was integrated with Elastic Stack and...