[sc name=”ad_1″] Using an Android device? Beware! You have to remain more caution while opening an image file on your smartphone—downloaded...
Search Results For - Vulnerable Apps
[sc name=”ad_1″] Google has finally patched a privacy vulnerability in its Chrome web browser for Android that exposes users’ device model...
[sc name=”ad_1″] Google today revealed that Google+ has suffered another massive data breach, forcing the tech giant to shut down its struggling...
[sc name=”ad_1″] The United States Postal Service has patched a critical security vulnerability that exposed the data of more than 60 million...
[sc name=”ad_1″] A widely used third-party NodeJS module with nearly 2 million downloads a week was compromised after one of its open-source...
Airbash is a POSIX-compliant, fully automated WPA PSK handshake capture script aimed at penetration testing. It is compatible with Bash and Android Shell...
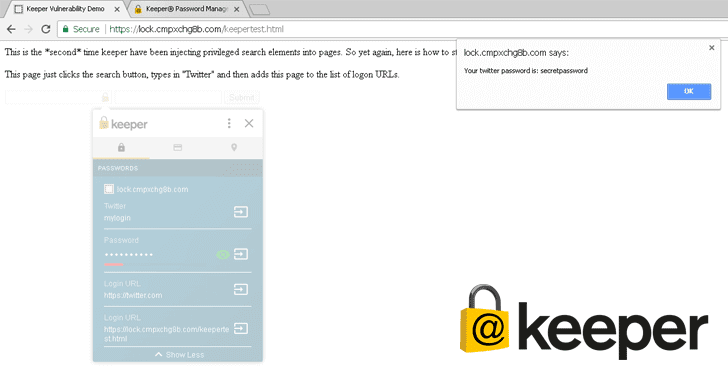
If you are running Windows 10 on your PC, then there are chances that your computer contains a pre-installed 3rd-party password manager app that lets attackers...
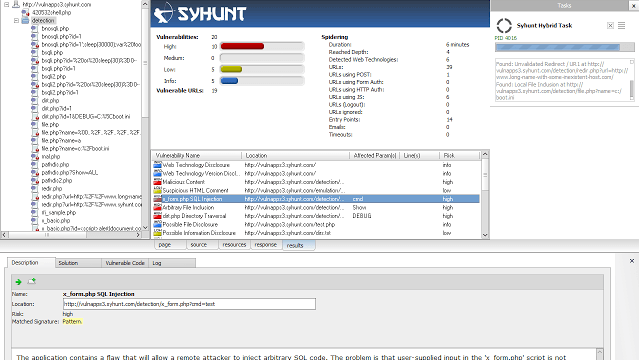
Syhunt ScanTools 6.0 adds advanced fingerprinting capabilities, enhanced spidering, injection and code scan capabilities, and a large number of improved checks...
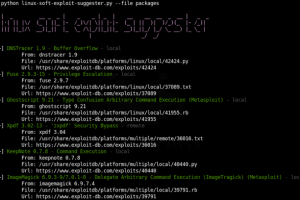
linux-soft-exploit-suggester finds exploits for all vulnerable software in a system helping with the privilege escalation. It focuses on software packages...
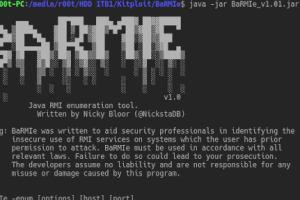
BaRMIe is a tool for enumerating and attacking Java RMI (Remote Method Invocation) services. RMI services often expose dangerous functionality without adequate...