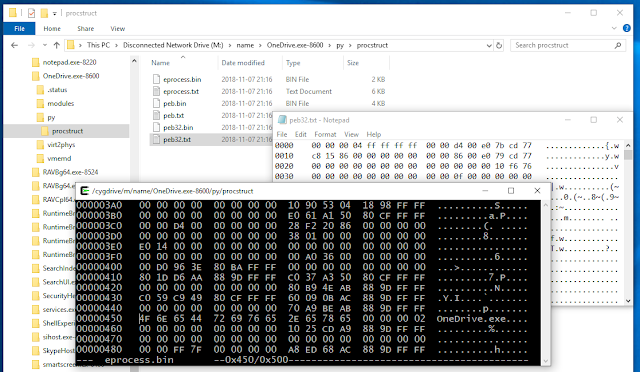
[sc name=”ad_1″] The Memory Process File System is an easy and convenient way of accessing physical memory as files a virtual file system. Easy...
Search Results For - Vulnerability
[sc name=”ad_1″] A File Inclusion & Directory Traversal fuzzing, enumeration & exploitation tool. FDsploit menu: $ python fdsploit.py -h...
[sc name=”ad_1″] Scout Suite is an open source multi-cloud security-auditing tool, which enables security posture assessment of cloud environments...
[sc name=”ad_1″] It is utmost important for any security engineer to understand their network first before securing it and it becomes a daunting...
[sc name=”ad_1″] BOtB is a container analysis and exploitation tool designed to be used by pentesters and engineers while also being CI/CD friendly...
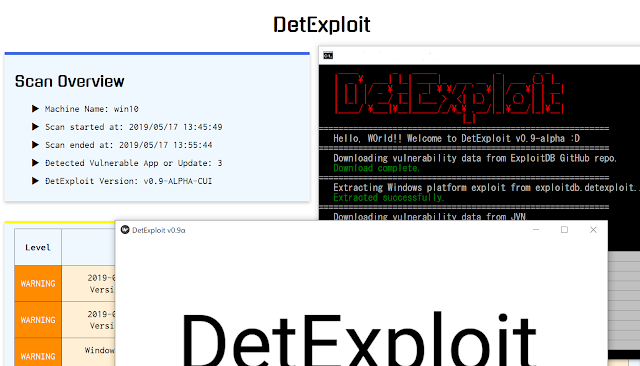
[sc name=”ad_1″] DetExploit is software that detect vulnerable applications and not-installed important OS updates on the system, and notify them...
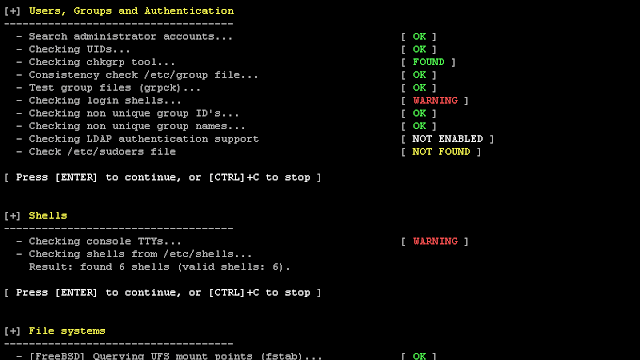
[sc name=”ad_1″] We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of...
[sc name=”ad_1″] The popular SSH client program PuTTY has released the latest version of its software that includes security patches for 8 high...
[sc name=”ad_1″] Security researchers have uncovered a new variant of the infamous Mirai Internet of Things botnet, this time targeting embedded...
[sc name=”ad_1″] Libssh2, a popular open source client-side C library implementing the SSHv2 protocol, has released the latest version of its...