[sc name=”ad_1″] A serious security vulnerability has been discovered in the core runC container code that affects several open-source container...
Search Results For - Vulnerability Management
[sc name=”ad_1″] If the connectivity and security of your organization rely on Cisco RV320 or RV325 Dual Gigabit WAN VPN routers, then you need to...
[sc name=”ad_1″] A massive government data belonging to the Oklahoma Department of Securities (ODS) was left unsecured on a storage server for at...
[sc name=”ad_1″] Cybersecurity researchers have discovered a critical vulnerability in widely used SQLite database software that exposes billions...
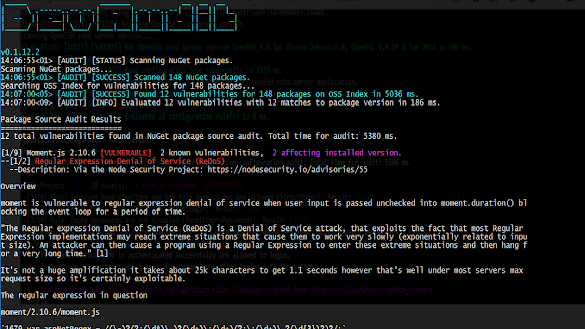
[sc name=”ad_1″] DevAudit is an open-source, cross-platform, multi-purpose security auditing tool targeted at developers and teams adopting DevOps...
[sc name=”ad_1″] dawnscanner is a source code scanner designed to review your ruby code for security issues. dawnscanner is able to scan plain ruby...
[sc name=”ad_1″] Developers of phpMyAdmin, one of the most popular and widely used MySQL database management systems, today released an updated...
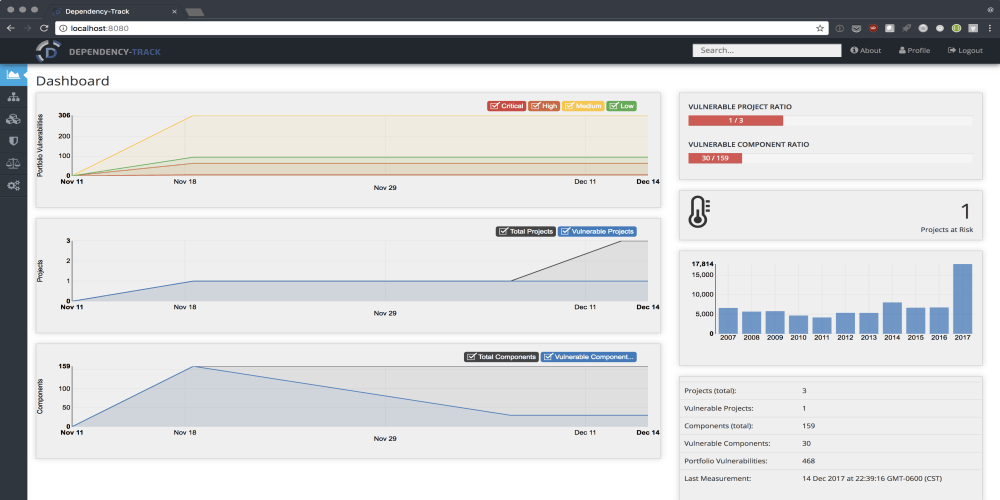
Modern applications leverage the availability of existing components for use as building blocks in application development. By using existing components...
Amongst the most common and in demand applications for MySQL database management is the phpMyAdmin, which became vulnerable, when a critical flaw was found in...
The security vulnerability was discovered in the Linksys WVBR0-25 wireless video bridge, which was designed to enable the main Genie DVR to communicate over...