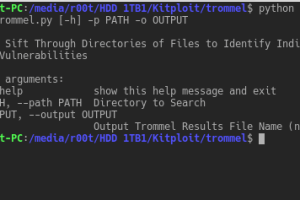
TROMMEL sifts through directories of files to identify indicators that may contain vulnerabilities. TROMMEL identifies the following indicators related to:...
Search Results For - Vulnerability Analysis
Hey Guys, In this video i show you a great tool called Yuki Chan. The Yuki Chan is an Automated Penetration Testing tool this tool will auditing all standard...
[sc name=”ad_1″] Watcher is a Django & React JS automated platform for discovering new potentially cybersecurity threats targeting your...
[sc name=”ad_1″] Process Herpaderping is a method of obscuring the intentions of a process by modifying the content on disk after the image has...
[sc name=”ad_1″] For the most up-to-date information on Anchore Engine, Anchore CLI, and other Anchore software, please refer to the Anchore...
[sc name=”ad_1″] A proof of concept crypto virus to spread user awareness about attacks and implications of ransomwares. Phirautee is written...
[sc name=”ad_1″] Spyse is a cybersecurity search engine for finding technical information about different internet entities, business data, and...
[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...
[sc name=”ad_1″] FATT is a script for extracting network metadata and fingerprints such as JA3 and HASSH from packet capture files (pcap) or live...
[sc name=”ad_1″] Lockdoor Framework : A Penetration Testing Framework With Cyber Security Resources. 09/2019 : 1.0Beta Information Gathring Tools...