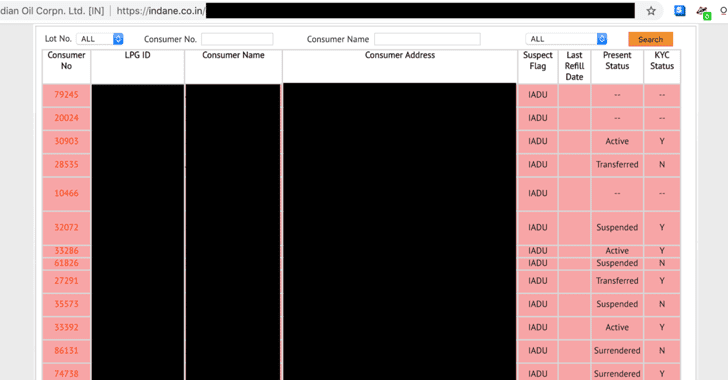
[sc name=”ad_1″] It is utmost important for any security engineer to understand their network first before securing it and it becomes a daunting...
Search Results For - Twitter
[sc name=”ad_1″] gitGraber is a tool developed in Python3 to monitor GitHub to search and find sensitive data for different online services such...
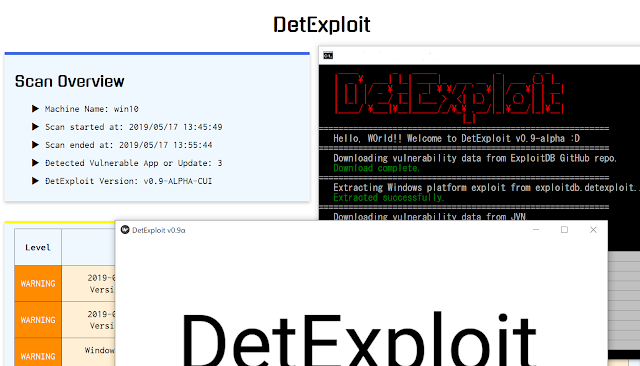
[sc name=”ad_1″] DetExploit is software that detect vulnerable applications and not-installed important OS updates on the system, and notify them...
[sc name=”ad_1″] Security researchers have uncovered a new variant of the infamous Mirai Internet of Things botnet, this time targeting embedded...
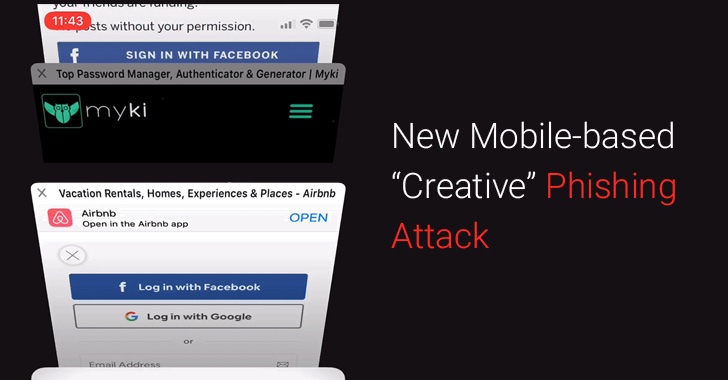
[sc name=”ad_1″] A cybersecurity researcher who last month warned of a creative phishing campaign has now shared details of a new but similar...
[sc name=”ad_1″] The United States’ National Security Agency (NSA) today finally released GHIDRA version 9.0 for free, the agency’s home...
[sc name=”ad_1″] It’s not just the critical Drupal vulnerability that is being exploited by in the wild cybercriminals to attack vulnerable...
[sc name=”ad_1″] A low interaction honeypot with the capability to be more of a medium interaction honeypot. HoneyPy is written in Python2 and is...
[sc name=”ad_1″] Why would someone bother to hack a so-called “ultra-secure encrypted database that is being protected behind 13 feet high...
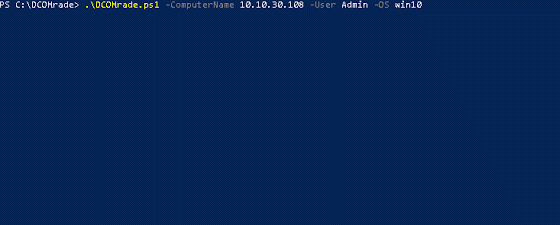
[sc name=”ad_1″] DCOMrade is a Powershell script that is able to enumerate the possible vulnerable DCOM applications that might allow for...