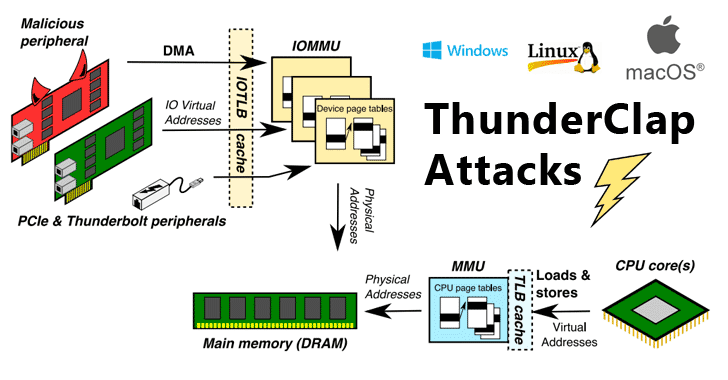
[sc name=”ad_1″] Security researchers have discovered a new class of security vulnerabilities that impacts all major operating systems, including...
Search Results For - Threat
[sc name=”ad_1″] It’s not just the critical Drupal vulnerability that is being exploited by in the wild cybercriminals to attack vulnerable...
[sc name=”ad_1″] How do you know whether an attacker has infiltrated your network? Can you really rely on an Endpoint Detection and Response (EDR)...
[sc name=”ad_1″] It’s not at all surprising that downloading movies and software from the torrent network could infect your computer with...
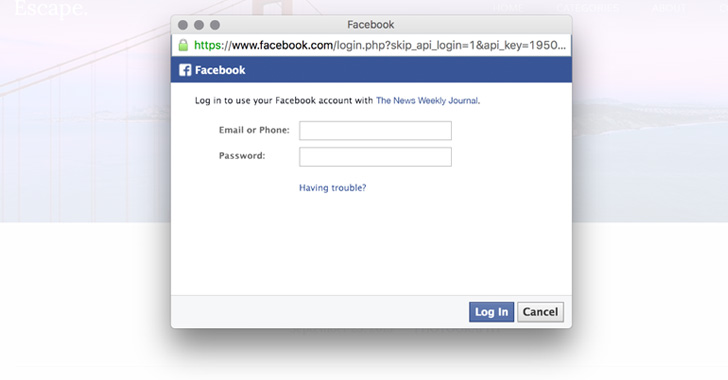
[sc name=”ad_1″] How do you check if a website asking for your credentials is fake or legit to log in? By checking if the URL is correct? By...
[sc name=”ad_1″] Cybersecurity researchers have discovered a way to hide malicious code in Intel SGX enclaves, a hardware-based memory encryption...
[sc name=”ad_1″] The United States Department of Justice (DoJ) announced Wednesday its effort to “map and further disrupt” a botnet...
[sc name=”ad_1″] Security researchers have discovered two separate malware campaigns, one of which is distributing the Ursnif data-stealing trojan...
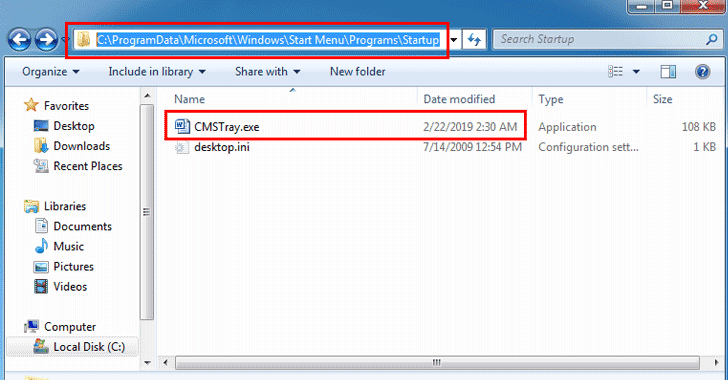
[sc name=”ad_1″] It is 2019, and millions of computers still either have at least one outdated application installed or run outdated operating...
[sc name=”ad_1″] The U.S. Department of Homeland Security (DHS) has today issued an “emergency directive” to all federal agencies...