[sc name=”ad_1″] The Department of Justice announced Wednesday charges against two Iranian nationals for their involvement in creating and...
Search Results For - Threat
[sc name=”ad_1″] Cybersecurity researchers have discovered a new zero-day vulnerability in Adobe Flash Player that hackers are actively exploiting...
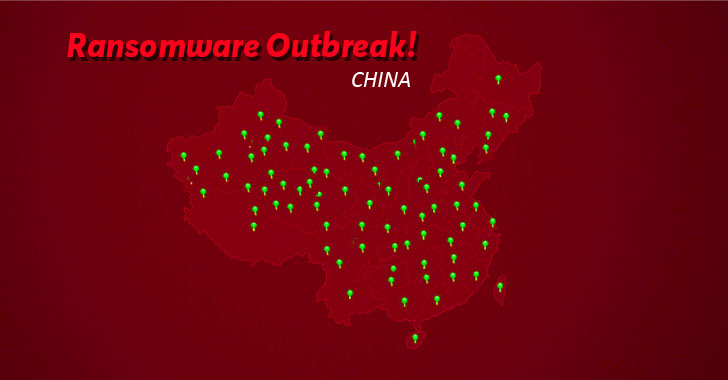
A new piece of ransomware is spreading rapidly across China that has already infected more than 100,000 computers in the last four days as a result of a supply...
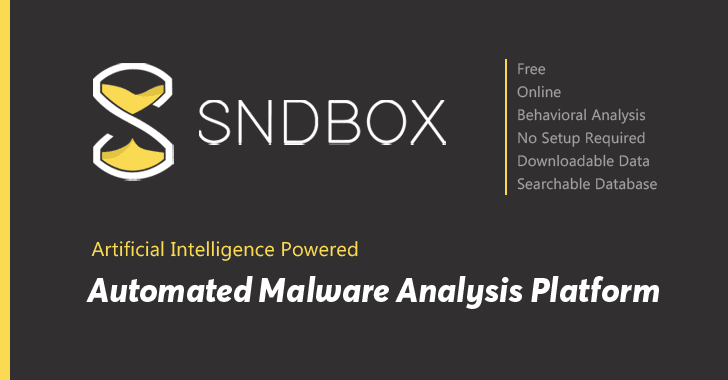
Looking for an automated malware analysis software? Something like a 1-click solution that doesn’t require any installation or configuration…a...
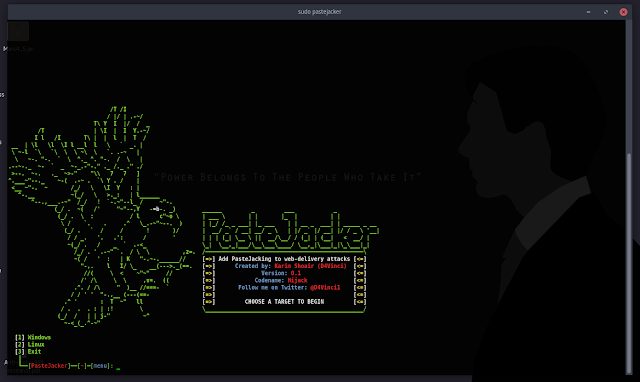
The main purpose of the tool is automating (PasteJacking/Clipboard poisoning/whatever you name it) attack with collecting all the known tricks used in this...
Cybersecurity firm FireEye claims to have discovered evidence that proves the involvement of a Russian-owned research institute in the development of the...
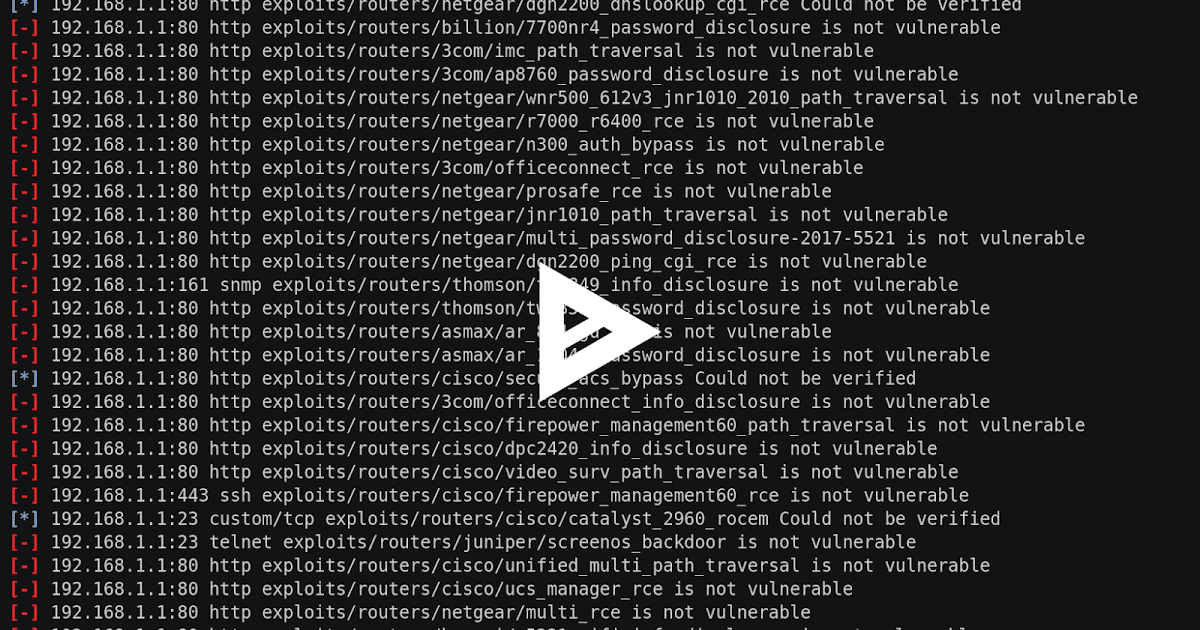
The RouterSploit Framework is an open-source exploitation framework dedicated to embedded devices. It consists of various modules that aids penetration testing...
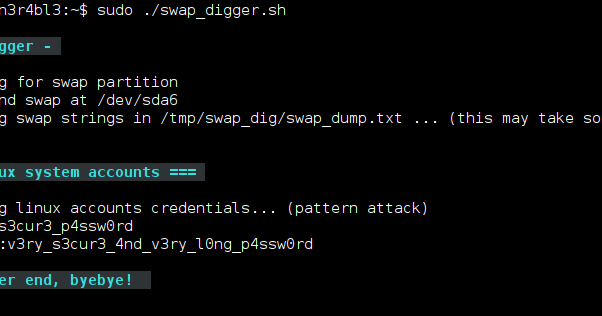
swap_digger is a bash script used to automate Linux swap analysis for post-exploitation or forensics purpose. It automates swap extraction and searches for...
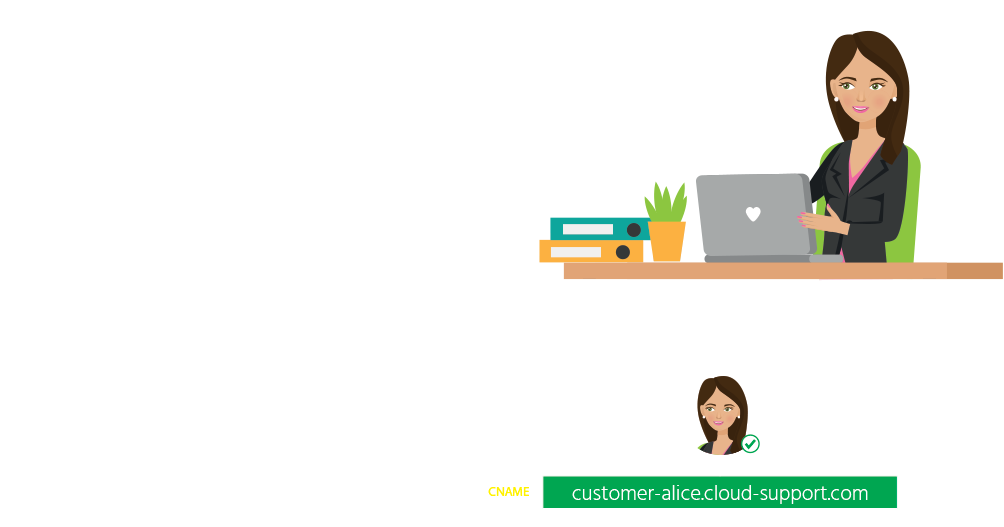
Domain Hijacking is a well-known security issue that can be carried in many different ways. In addition to social engineering or unauthorized access to the...
Despite countless examples to the contrary, many people still toss cryptocurrency and criminal activity into the same bucket. But is this born out of ignorance...