[sc name=”ad_1″] VBScript minifier Features Remove extra whitespace Trailing whitespace Leading whitespace Blank lines Inline extra spaces Remove...
Search Results For - Stealth
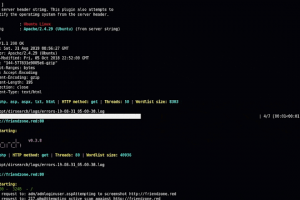
[sc name=”ad_1″] Enumerate a target Based off of Nmap Results Features The purpose of O.G. Auto-Recon is to automate the initial information...
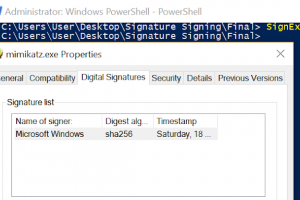
[sc name=”ad_1″] Hijacking legitimate digital signatures is a technique that can be used during red team assessments in order to sign PowerShell...
[sc name=”ad_1″] How it works Scan common ports Send a TCP Syn packet to the destination on the defined port, if the port is open, use an nmap scan...
[sc name=”ad_1″] A Undetectable Payload Generation. This tool is for educational purpose only, usage of Kaiten for attacking targets without prior...
[sc name=”ad_1″] HRShell: An advanced HTTP(S) Reverse Shell built with Flask HRShell is an HTTPS/HTTP reverse shell built with flask. It’s...
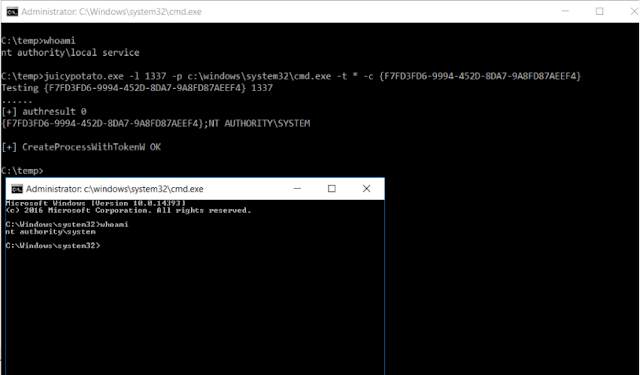
[sc name=”ad_1″] A sugared version of RottenPotatoNG, with a bit of juice, i.e. another Local Privilege Escalation tool, from a Windows Service...
[sc name=”ad_1″] Dolos Cloak is a python script designed to help network penetration testers and red teamers bypass 802.1x solutions by using an...
[sc name=”ad_1″] A team of cybersecurity researchers from the University of New Haven yesterday released a video demonstrating how vulnerabilities...
[sc name=”ad_1″] Since most security tools also keep an eye on the network traffic to detect malicious IP addresses, attackers are increasingly...