The flaw has been discovered by security researchers from the University of Birmingham, who tested hundreds of various banking applications and discovered that...
Search Results For - Secure
After rapidly reinforcing a flaw that acknowledged anyone with access to a High Sierra Mac to take administrative control, Apple still has extra work to do to...
It had earlier banned an internet-associated doll called, My Friend Cayla, for similar reasons. Telecoms regulator the Federal Network Agency urged parents who...
Newly uncovered vulnerabilities in a popular brand of indoor internet-connected cameras could be exploited by attackers in order to gain complete control of...
The tool itself is impressive enough, serving as the backbone of the CIA’s malware processes, but there’s more. What’s interesting about the first leak in the...
Today, 9 November 2017, WikiLeaks publishes the source code and development logs to Hive, a major component of the CIA infrastructure to control its malware...
Security GNU/Linux distribution designed with cloud pentesting and IoT security in mind. It includes a full portable laboratory for security and digital...
CrunchRAT currently supports the following features: File upload File download Command execution It is currently single-threaded (only one task at a time), but...
Easily launch a new phishing site fully presented with SSL and capture credentials along with 2FA tokens using CredSniper. The API provides secure access to...
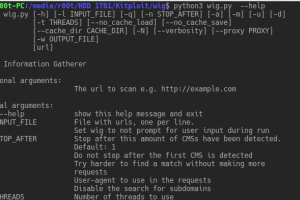
wig is a web application information gathering tool, which can identify numerous Content Management Systems and other administrative applications. The...