A 21-year-old Kentucky man who previously pleaded guilty to developing, marketing, and selling an infamous remote access trojan (RAT) called LuminosityLink has...
Search Results For - Secure
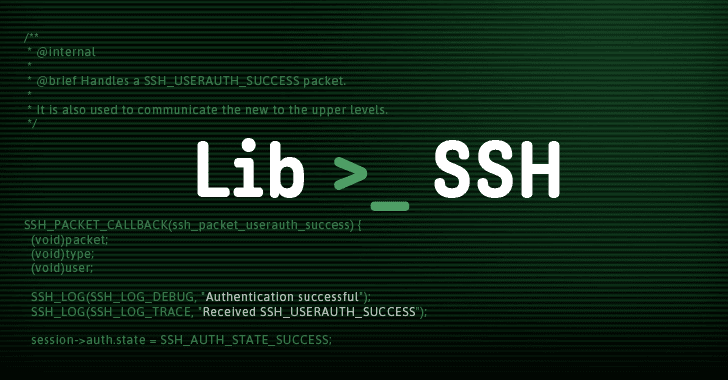
A four-year-old severe vulnerability has been discovered in the Secure Shell (SSH) implementation library known as Libssh that could allow anyone to completely...
All major web browsers, including Google Chrome, Apple Safari, Microsoft Edge, Internet Explorer, and Mozilla Firefox, altogether today announced to soon...
In an effort to secure users’ data while maintaining privacy, Google has announced a new security measure for Android Backup Service that now encrypts...
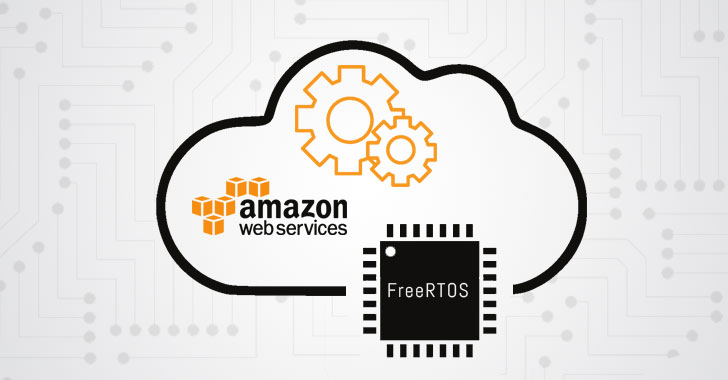
A security researcher has discovered several critical vulnerabilities in one of the most popular embedded real-time operating systems—called FreeRTOS—and its...
An Indian security researcher has discovered a highly critical flaw in X.Org Server package that impacts OpenBSD and most Linux distributions, including...
Discover sub-domains by searching through Certificate Transparency logs. What is CT? Certificate Transparency (CT) is an experimental IETF standard. The goal...
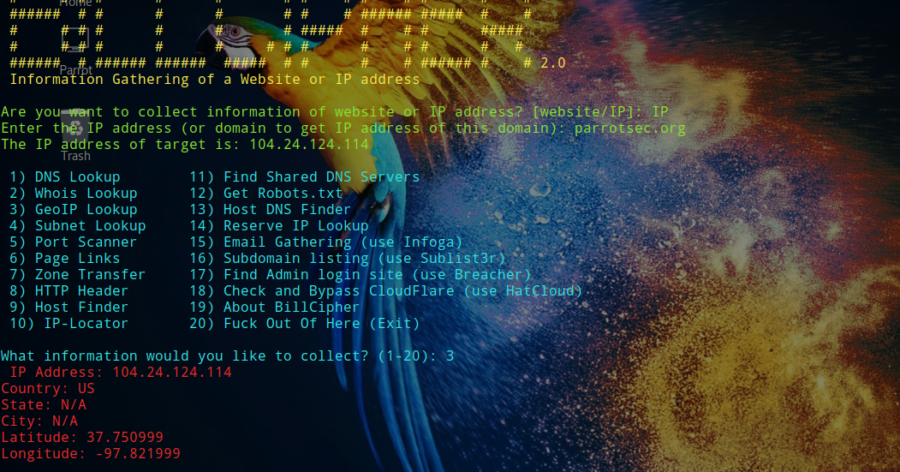
Information Gathering tool for a Website or IP address, use some ideas from Devploit. BillCipher can work in any operating system if they have and support...
Cryptocurrencies such as Bitcoin have been gaining more and more public attention over recent years. Now, the digital currency industry has hit Hollywood with...
GlobaLeaks is open-source / free software intended to enable secure and anonymous whistleblowing initiatives developed by the Hermes Center for Transparency...