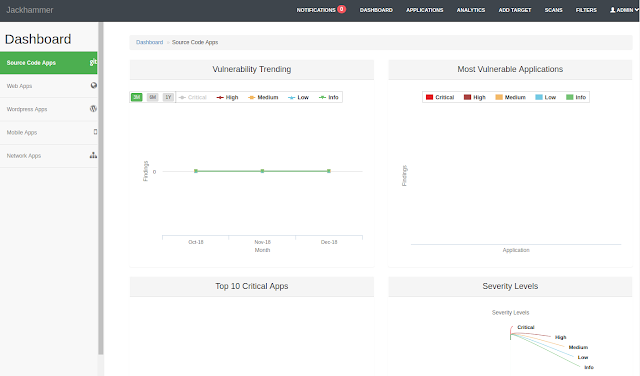
[sc name=”ad_1″] One Security vulnerability assessment/management tool to solve all the security team problems. What is Jackhammer? Jackhammer is a...
Search Results For - Secrets
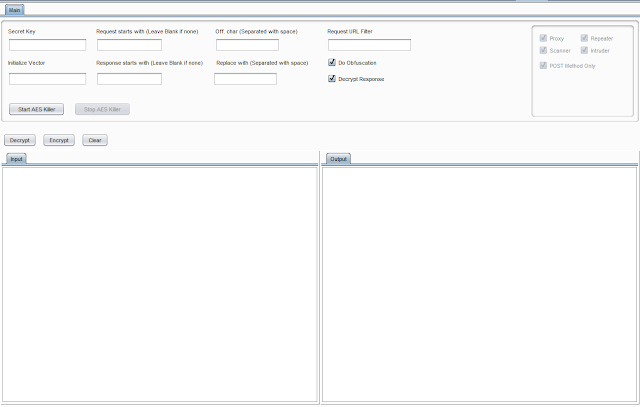
Burpsuite Plugin to decrypt AES Encrypted traffic on the fly. Requirements Burpsuite Java Tested on Burpsuite 1.7.36 Windows 10 xubuntu 18.04 Kali Linux 2018...
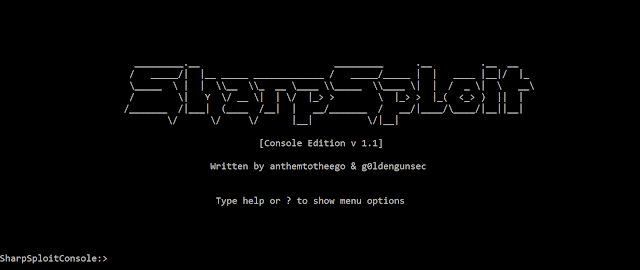
Console Application designed to interact with SharpSploit released by @cobbr_io SharpSploit is a tool written by @cobbr_io that combines many techniques/C#...
pspy is a command line tool designed to snoop on processes without need for root permissions. It allows you to see commands run by other users, cron jobs, etc...
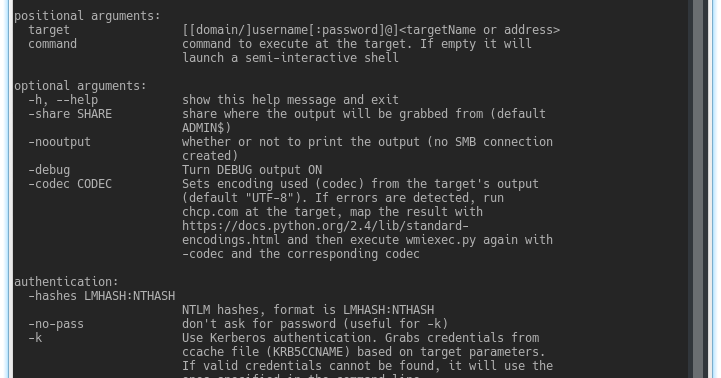
Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets...
M$ Windows Hacking Pack =========== Tools here are from different sources. The repo is generally licensed with WTFPL, but some content may be not (eg...
At last, Wi-Fi security — or lack of — is about to get its day in the sun. The Wi-Fi Alliance, an industry body made up of device makers including...
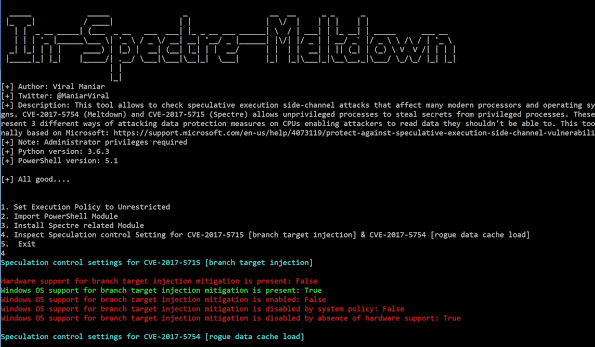
This tool allows to check speculative execution side-channel attacks that affect many modern processors and operating systems designs. CVE-2017-5754 (Meltdown)...
A former National Security Agency hacker has admitted to illegally taking highly classified information from the agency’s headquarters, which was later...
Apple uses the Tenth Anniversary iPhone X Phone to replace Touch ID. Because the award handset features an edge-to-edge protection and has very slim bezels...