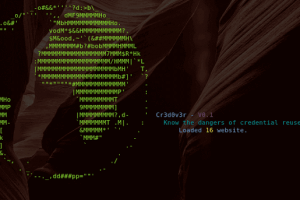
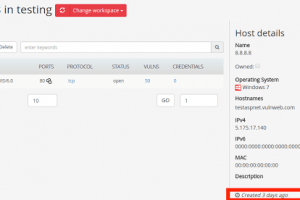
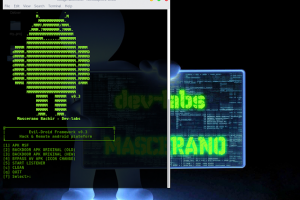
Your best friend in credential reuse attacks. Cr3dOv3r simply you give it an email then it does two simple jobs (but useful) : Search for public leaks for the...
Search Results For - Screenshot
Faraday is the Integrated Multiuser Risk Environment you have always been looking for! It maps and leverages all the data you generate in real time, letting...
Mentalist is a graphical tool for custom wordlist generation. It utilizes common human paradigms for constructing passwords and can output the full wordlist as...
Evil-Droid is a framework that create & generate & embed apk payload to penetrate android platforms. Screenshot: Dependencies : 1 - metasploit...
Striker is an offensive information and vulnerability scanner. Features Just supply a domain name to Striker and it will automatically do the following for...
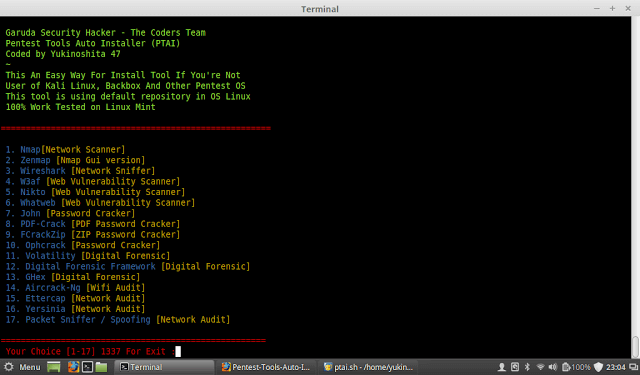
A Simple tool for installing pentest tools and forensic tools on Debian / Ubuntu Based OS Tested on Linux Mint And Kali Linux How To Do ?? Change Your...
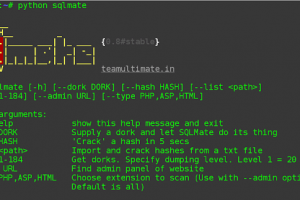
There are some features that we think SQLMap should have. Like finding admin panel of the target, better hash cracking etc. If you think the same, SQLMate is...
The official blog of jQuery—most popular JavaScript library used by millions of websites—has been hacked by some unknown hackers, using the pseudonym...
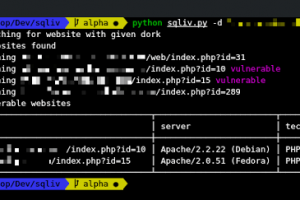
Massive SQL injection vulnerability scanner. Features multiple domain scanning with SQL injection dork by Bing, Google, or Yahoo targetted scanning by...
According to various cybersecurity firms, the growing virus is dubbed “BadRabbit” and is a form of ransomware that bolts down machines and requires bitcoin...