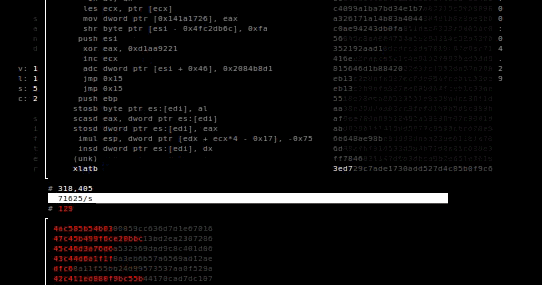
The sandsifter audits x86 processors for hidden instructions and hardware bugs, by systematically generating machine code to search through a processor’s...
Search Results For - Scanning
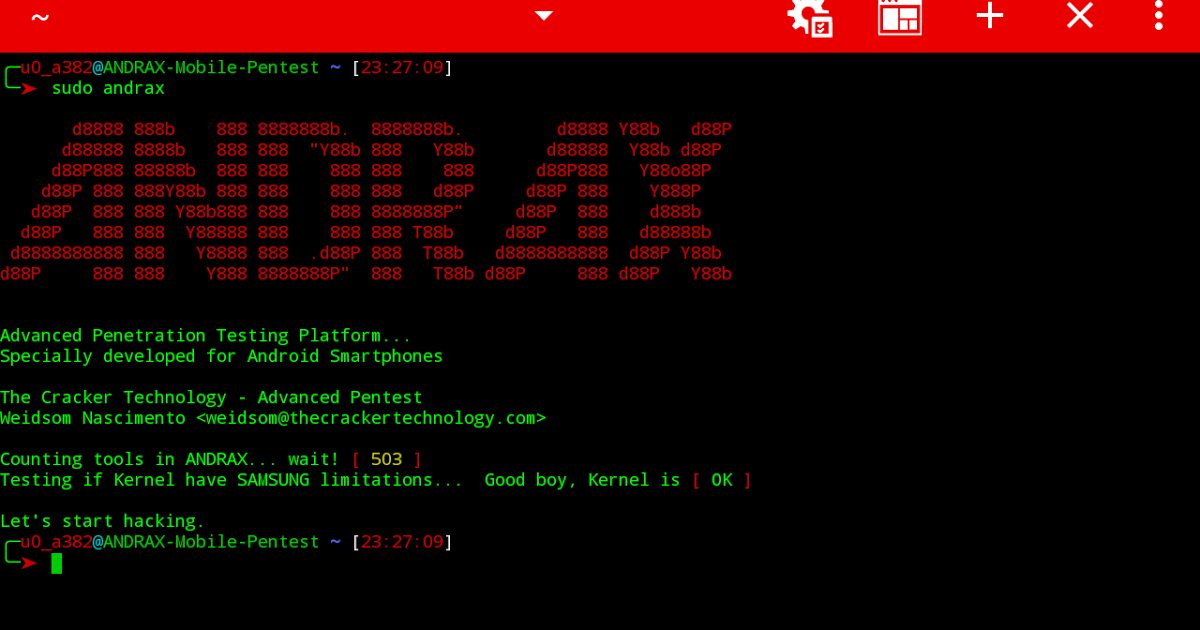
ANDRAX The first and unique Penetration Testing platform for Android smartphones What is ANDRAX ANDRAX is a penetration testing platform developed specifically...
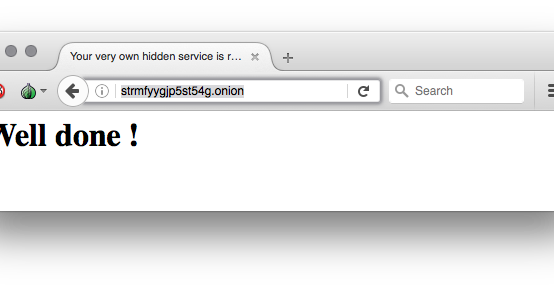
Easily run a hidden service inside the Tor network with this container Generate the skeleton configuration for you hidden service, replace for your hidden...
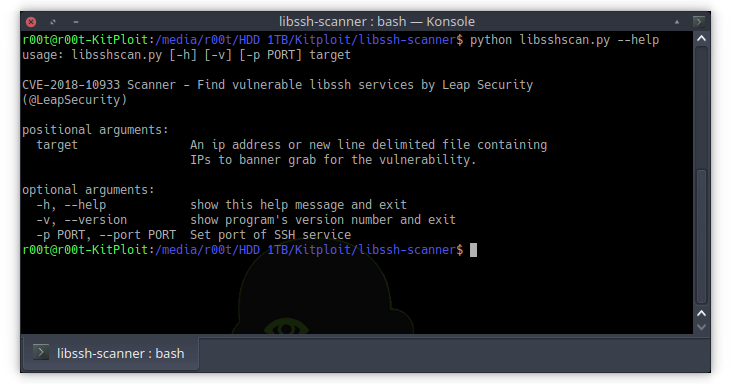
This is a python based script to identify hosts vulnerable to CVE-2018-10933. The vulnerability is present on versions of libssh 0.6+ and was remediated by a...
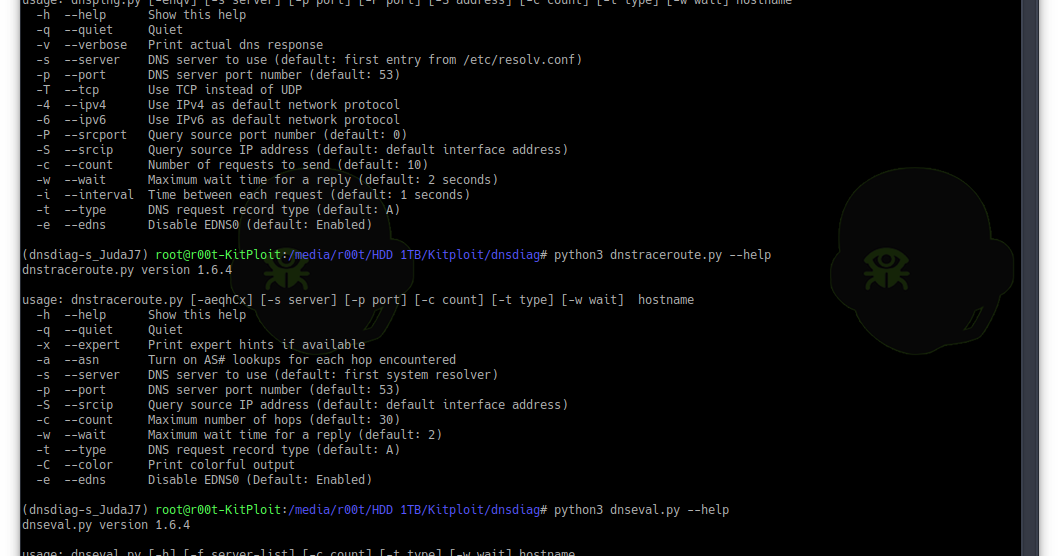
Ever been wondering if your ISP is hijacking your DNS traffic? Ever observed any misbehavior with your DNS responses? Ever been redirected to wrong address and...
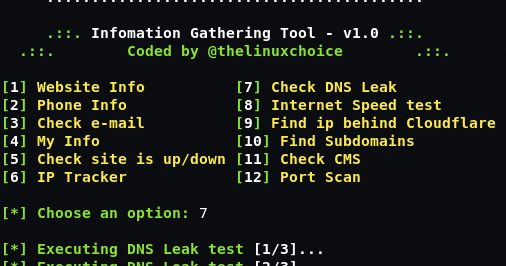
InfoG is a Shellscript to perform Information Gathering. Features Check Website info Check Phone info IP Tracker Check Valid E-mail Check if site is Up/Down...
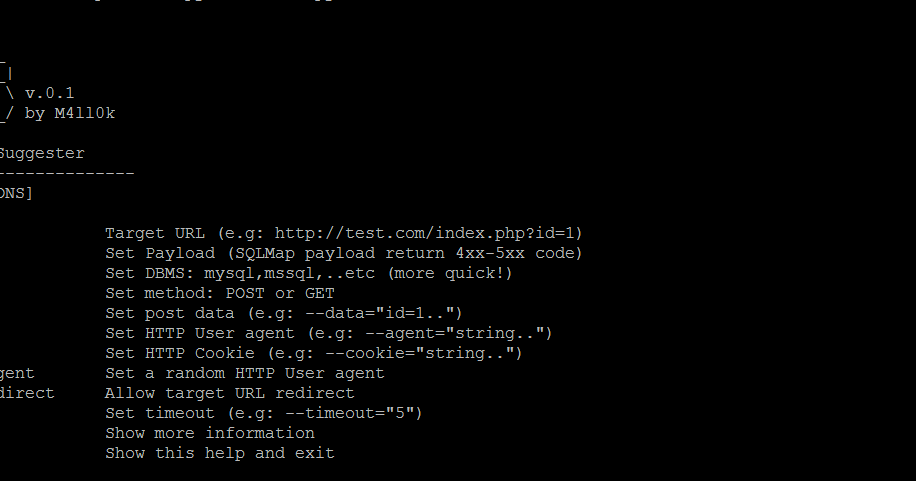
Atlas is an open source tool that can suggest sqlmap tampers to bypass WAF/IDS/IPS, the tool is based on returned status code. Screen Installation $ git clone...
A post-exploitation agent powered by Python, IronPython, C#/.NET. Requirements Server requires Python >= 3.7 SILENTTRINITY C# implant requires .NET >= 4...
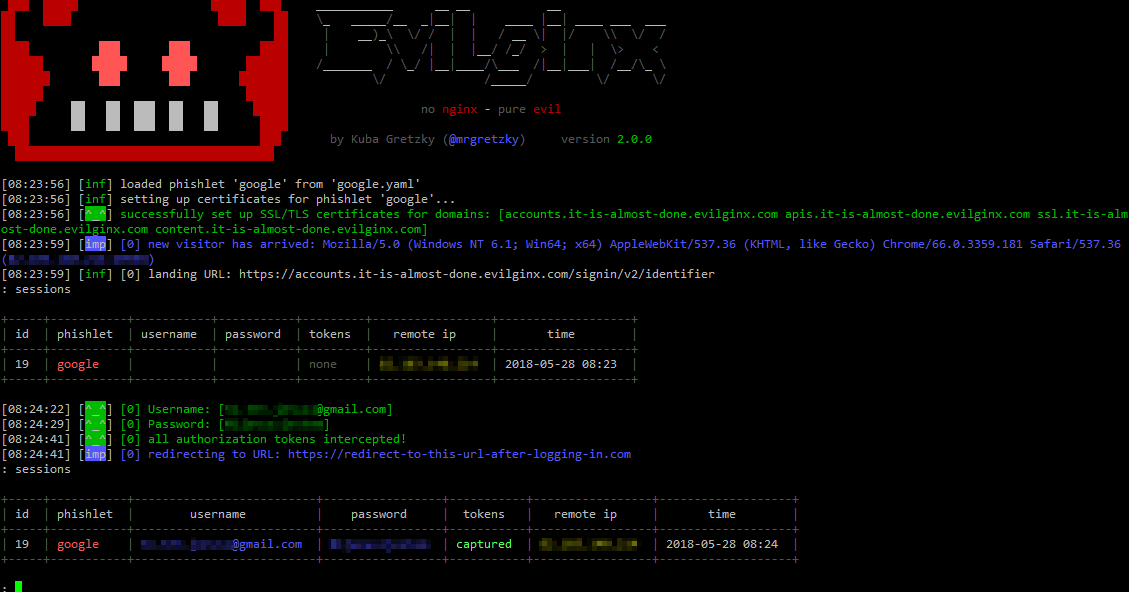
evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor...
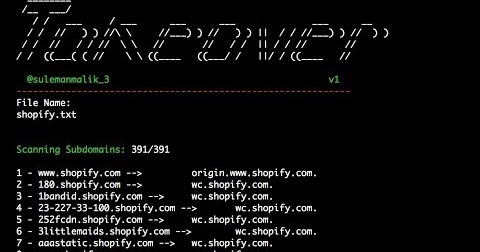
What is Subdomain Takeover? Subdomain takeover is a class of vulnerability where subdomain points to an external service that has been deleted. The external...