[sc name=”ad_1″] Exclusive — If you have not updated your website to the latest WordPress version 5.0.3, it’s a brilliant idea to upgrade the...
Search Results For - Scan
[sc name=”ad_1″] Smart devices definitely make our lives easier, faster, and more efficient, but unfortunately, an insecure smart device can also...
[sc name=”ad_1″] A malicious Windows EXE file can even infect your Mac computer as well. Yes, you heard me right — a .exe malware on macOS...
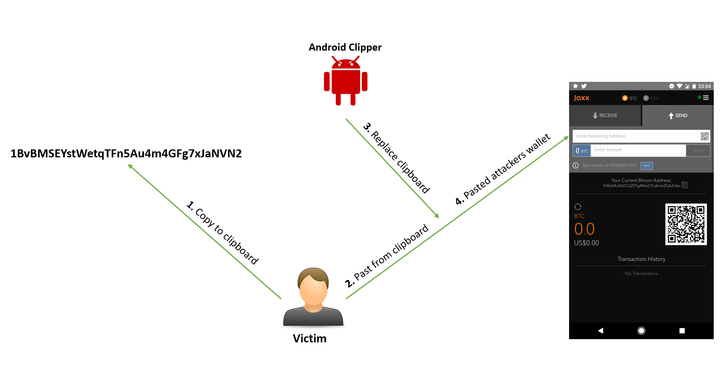
[sc name=”ad_1″] A security researcher has discovered yet another cryptocurrency-stealing malware on the official Google Play Store that was...
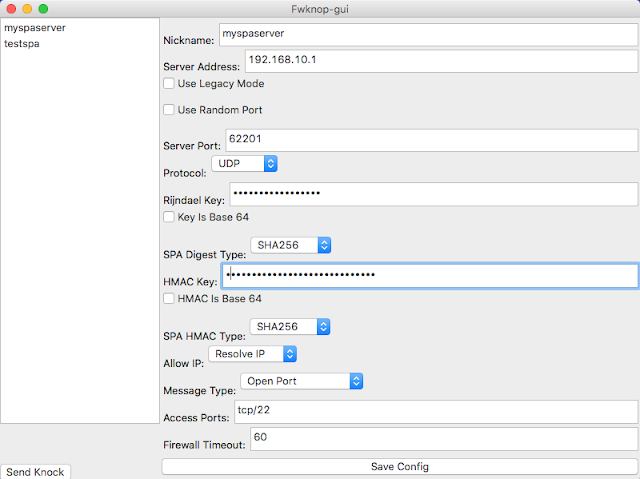
[sc name=”ad_1″] fwknop implements an authorization scheme known as Single Packet Authorization (SPA) for strong service concealment. SPA requires...
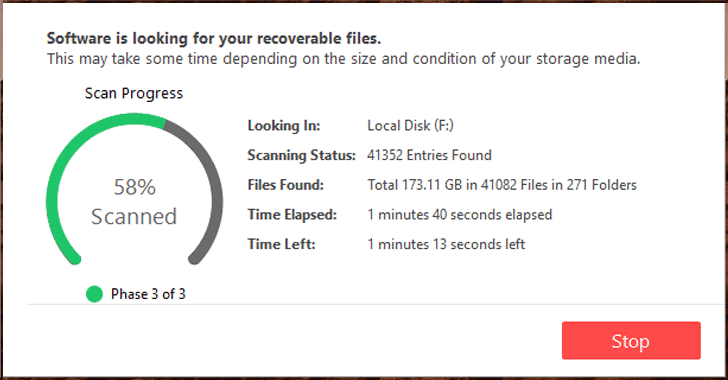
[sc name=”ad_1″] Have you ever lost your important files, like memories or official documents, accidentally or maliciously? Adding more… when...
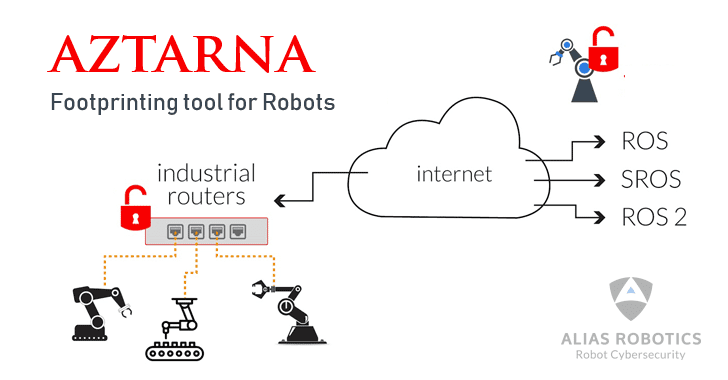
[sc name=”ad_1″] A team at a robot cybersecurity startup has released a free, open-source tool for information security professionals to help them...
[sc name=”ad_1″] If the connectivity and security of your organization rely on Cisco RV320 or RV325 Dual Gigabit WAN VPN routers, then you need to...
[sc name=”ad_1″] Even after so many efforts by Google for preventing its Play Store from malware, shady apps somehow managed to fool its anti...
[sc name=”ad_1″] Ukrainian Police have this week busted out two separate groups of hackers involved in carrying out DDoS attacks against news...