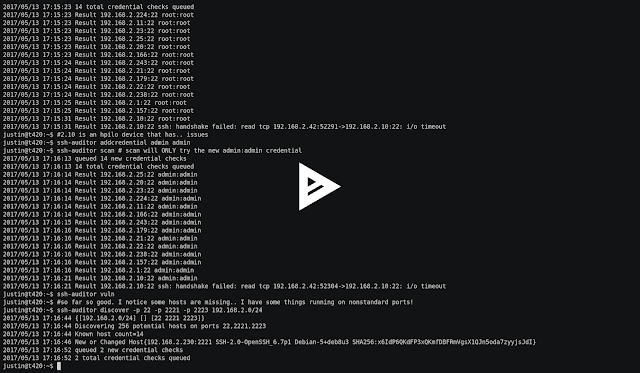
The Best Way To Scan For Weak Ssh Passwords On Your Network Features ssh-auditor will automatically: Re-check all known hosts as new credentials are added. It...
Search Results For - SSH server
Script to steal passwords from SSH. Install git clone cd sshLooter Configuration Edit the script on install.sh, and add your telegram bot api, and your userid...
[sc name=”ad_1″] ToothPicker is an in-process, coverage-guided fuzzer for iOS. It was developed to specifically targets iOS’s Bluetooth...
[sc name=”ad_1″] NERVE is a vulnerability scanner tailored to find low-hanging fruit level vulnerabilities, in specific application configurations...
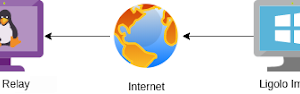
[sc name=”ad_1″] Ligolo is a simple and lightweight tool for establishing SOCKS5 or TCP tunnels from a reverse connection in complete safety (TLS...
[sc name=”ad_1″] The popular SSH client program PuTTY has released the latest version of its software that includes security patches for 8 high...
Scannerl is a modular distributed fingerprinting engine implemented by Kudelski Security. Scannerl can fingerprint thousands of targets on a single host, but...
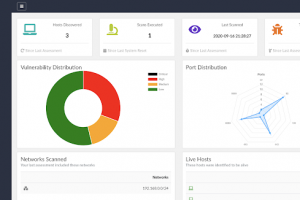
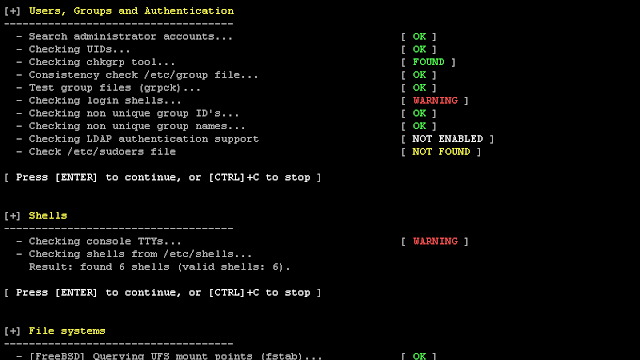
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next...
This project is a Docker image useful for solving Steganography challenges as those you can find at CTF platforms like hackthebox.eu. The image comes...
Features Auto VoIP/UC penetration test Report generation Performance RFC compliant SIP TLS and IPv6 support SIP over websockets (and WSS) support (RFC 7118)...