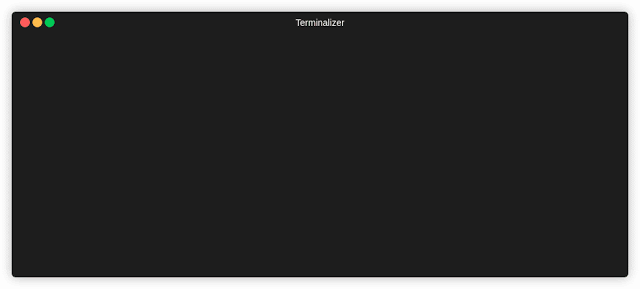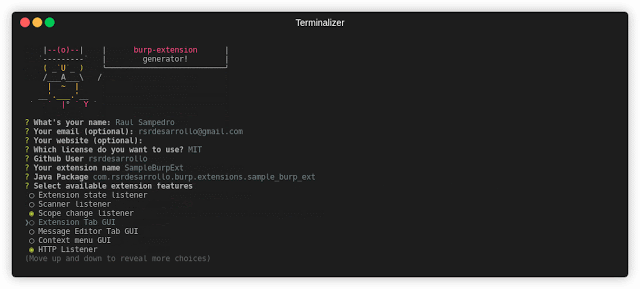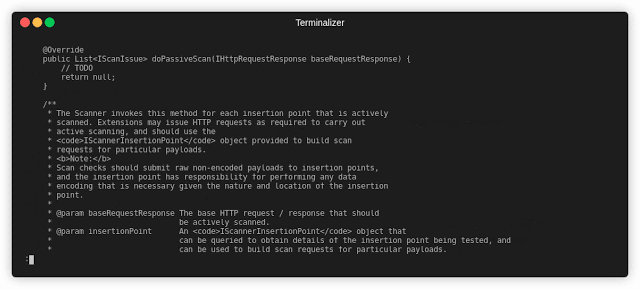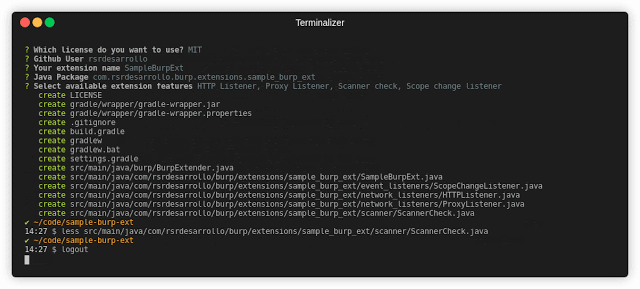
[sc name=”ad_1″] Everything You Need About Burp Extension Generation Installation First, install Yeoman and generator-burp-extension using npm (we...
Search Results For - Ruby
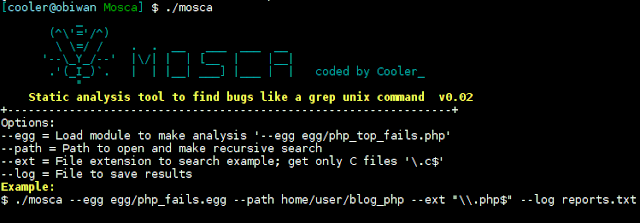
[sc name=”ad_1″] Mosca Manual analysis tool to find bugs like a grep unix command, Version 0.05 because is not dynamic… uses static code to...
[sc name=”ad_1″] Lockdoor Framework : A Penetration Testing Framework With Cyber Security Resources. 09/2019 : 1.0Beta Information Gathring Tools...
[sc name=”ad_1″] The Metasploit Project is a computer security project that provides information on vulnerabilities, helping in the development of...
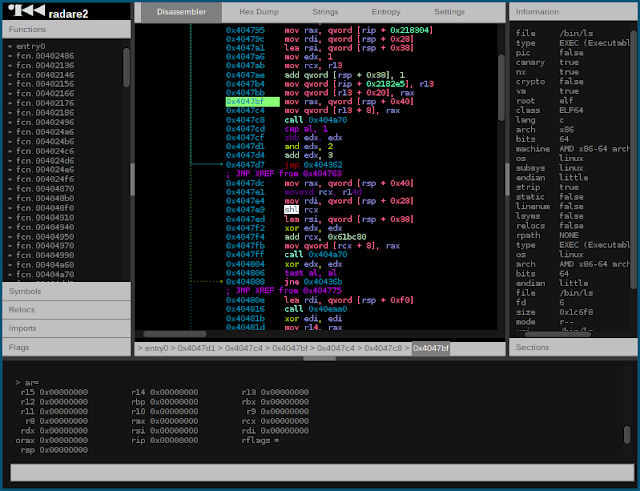
[sc name=”ad_1″] r2 is a rewrite from scratch of radare in order to provide a set of libraries and tools to work with binary files. Radare...
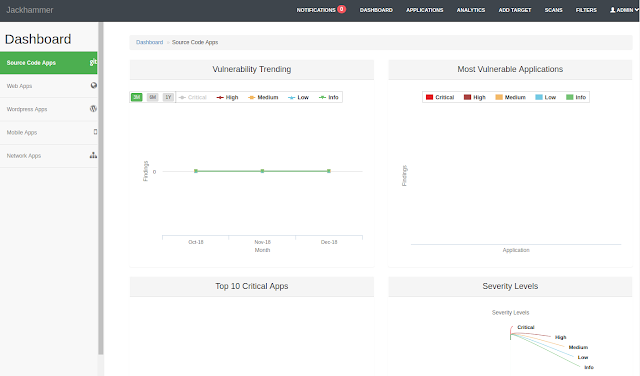
[sc name=”ad_1″] One Security vulnerability assessment/management tool to solve all the security team problems. What is Jackhammer? Jackhammer is a...
Scan WordPress, Drupal, Joomla, vBulletin websites for Security issues. CMSScan provides a centralized Security Dashboard for CMS Security scans. It is powered...
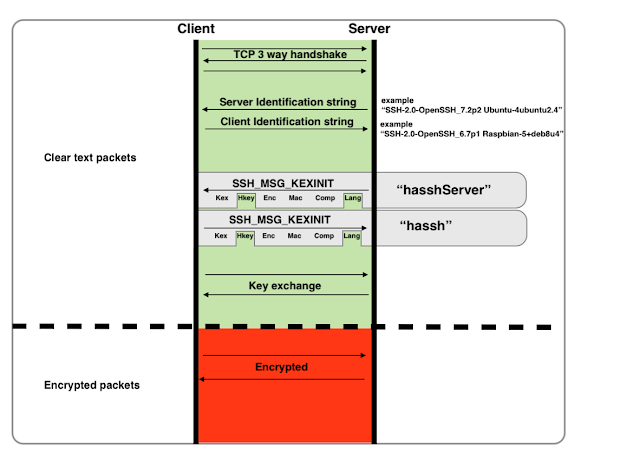
“HASSH” is a network fingerprinting standard which can be used to identify specific Client and Server SSH implementations. The fingerprints can be...
novahot is a webshell framework for penetration testers. It implements a JSON-based API that can communicate with trojans written in any language. By default...
Armor is a simple Bash script designed to create encrypted macOS payloads capable of evading antivirus scanners. Below is an example gif of Armor being used...