[sc name=”ad_1″] WhatsApp, Facebook, and Instagram faced a widespread outage yesterday with users from around the world reporting issues with...
Search Results For - Restrictions
[sc name=”ad_1″] You must update your Google Chrome immediately to the latest version of the web browsing application. Security researcher Clement...
[sc name=”ad_1″] A new security vulnerability has been discovered in the latest version of Apple’s macOS Mojave that could allow a malicious...
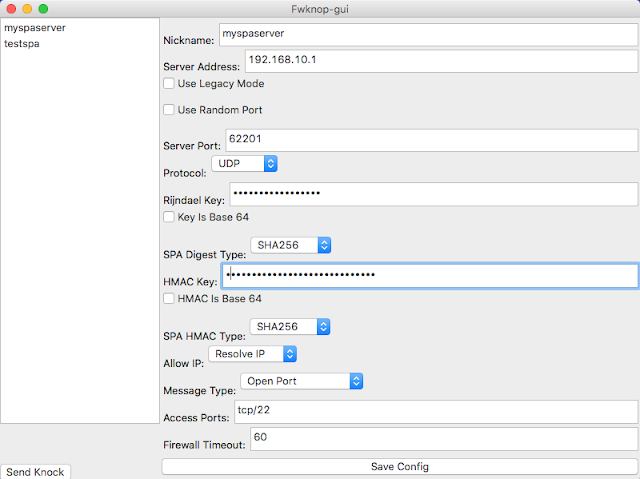
[sc name=”ad_1″] fwknop implements an authorization scheme known as Single Packet Authorization (SPA) for strong service concealment. SPA requires...
[sc name=”ad_1″] Good news, the new Kickass Torrents site is back. Back in July 2017, popular BitTorrent site Kickass Torrents (KAT cr) was taken...
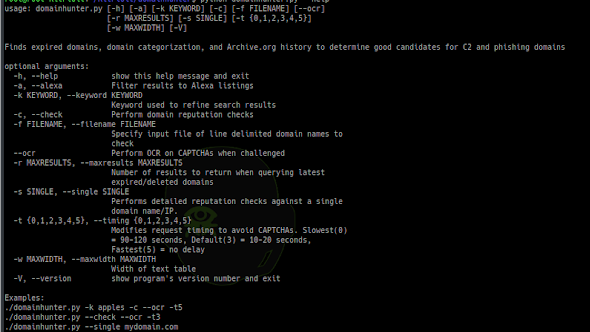
Domain name selection is an important aspect of preparation for penetration tests and especially Red Team engagements. Commonly, domains that were used...
[sc name=”ad_1″] It seems as though not a day goes by without a new story breaking about a high-level cyber attack on a major corporation or...
Weevely is a web shell designed for post-exploitation purposes that can be extended over the network at runtime. Upload weevely PHP agent to a target web...
SubFinder is a subdomain discovery tool that discovers valid subdomains for websites by using passive online sources. It has a simple modular architecture and...
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also...