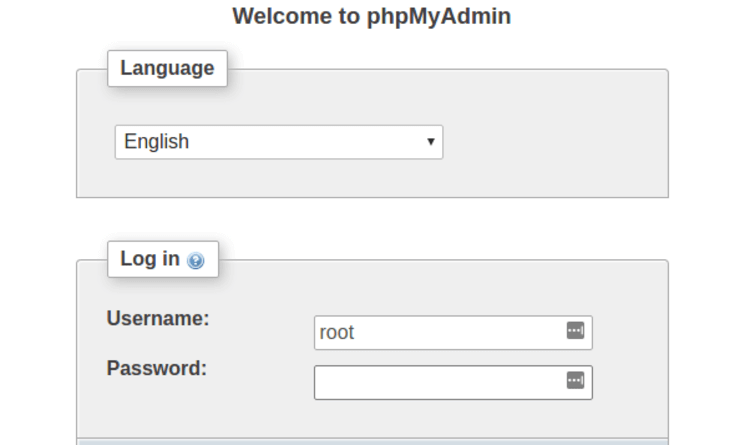
Amongst the most common and in demand applications for MySQL database management is the phpMyAdmin, which became vulnerable, when a critical flaw was found in...
Search Results For - Research
One of the biggest names in IT industry, Intel, has verified a report stating that some microprocessors have been built containing flaws in their design...
Defeating Google’s audio reCaptcha system with 85% accuracy. Inspiration Across the Internet, hundreds of thousands of sites rely on Google’s...
A security researcher (@s1guza) has published the details of an unpatched vulnerability in macOS that can be exploited to gain full control of a system. The...
Chiron is an IPv6 Security Assessment Framework, written in Python and employing Scapy. It is comprised of the following modules: • IPv6 Scanner • IPv6 Local...
This type of abusive conduct is possible because of a configuration flaw in the login handlers included with all browsers, login managers that allow browsers...
NTU researchers have revealed that smartphones can now be hacked using the data accumulated from sensors. Dr. Shivam, a scientist at NTU, who recently...
The administration of Guangzhou, center of the southern coastal province of Guangdong, began on Monday a pilot plan that creates a virtual ID card, which...
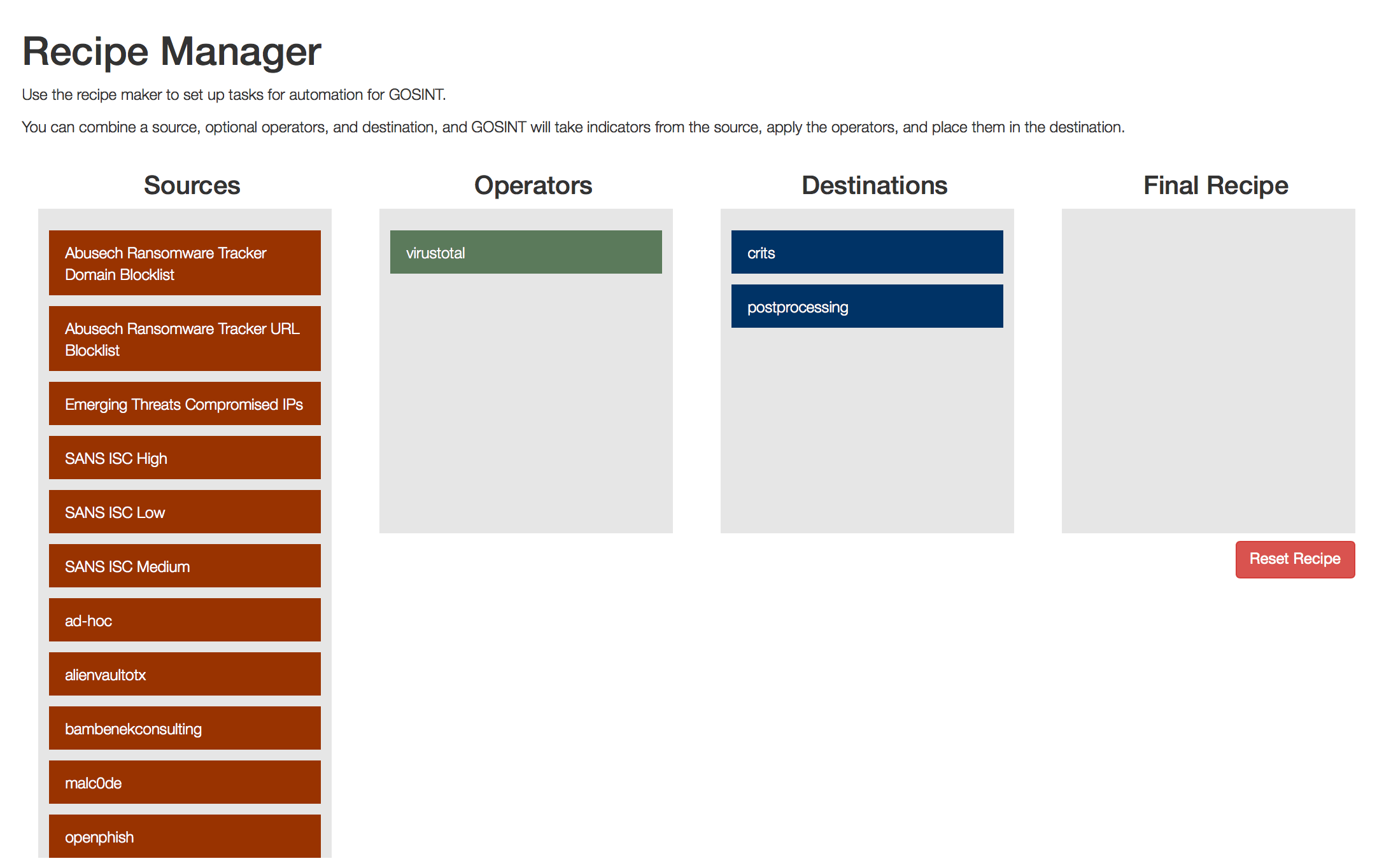
The GOSINT framework is a project used for collecting, processing, and exporting high quality indicators of compromise (IOCs). GOSINT allows a security analyst...
Most Android malware is at best annoying, but rarely does it cause physical damage to a phone. Not so with Loapi, a newly-discovered trojan with a...