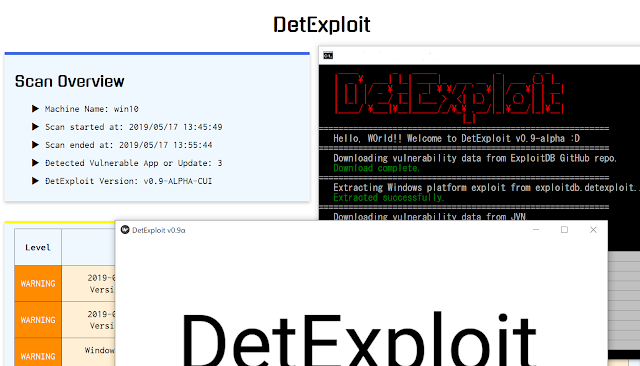
[sc name=”ad_1″] DetExploit is software that detect vulnerable applications and not-installed important OS updates on the system, and notify them...
Search Results For - Requirements
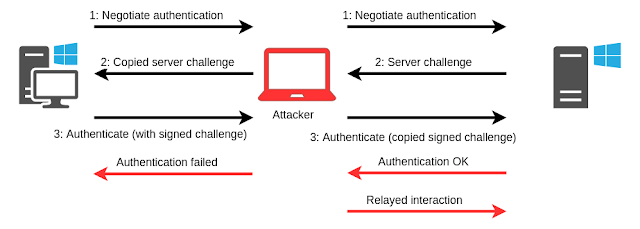
[sc name=”ad_1″] POC tools accompanying the blog Abusing Exchange: One API call away from Domain Admin. Requirements These tools require impacket...
[sc name=”ad_1″] This software project is a result of a Bachelor’s thesis created at SCHUTZWERK in collaboration with Aalen University by...
[sc name=”ad_1″] Synopsis bscan is a command-line utility to perform active information gathering and service enumeration. At its core, bscan...
[sc name=”ad_1″] The French data protection watchdog CNIL has issued its first fine of €50 million (around $57 million) under the European...
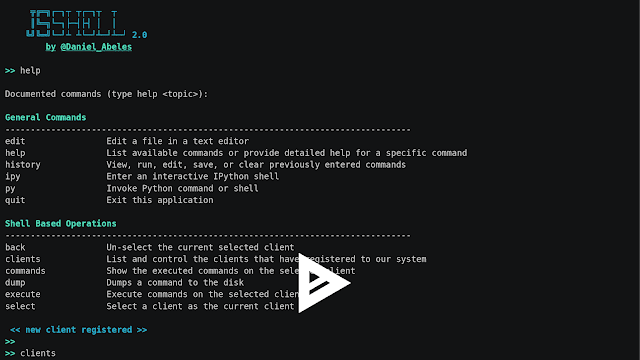
[sc name=”ad_1″] An interactive multi-user web based javascript shell. It was initially created in order to debug remote esoteric browsers during...
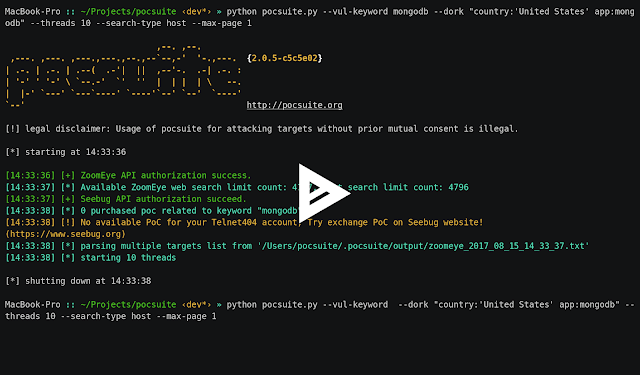
[sc name=”ad_1″] Pocsuite is an open-sourced remote vulnerability testing and proof-of-concept development framework developed by the Knownsec...
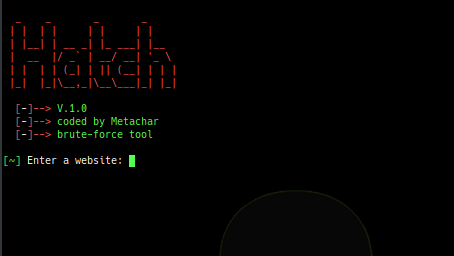
[sc name=”ad_1″] Hatch is a brute force tool that is used to brute force most websites Installation Instructions git clone python2 main.py...
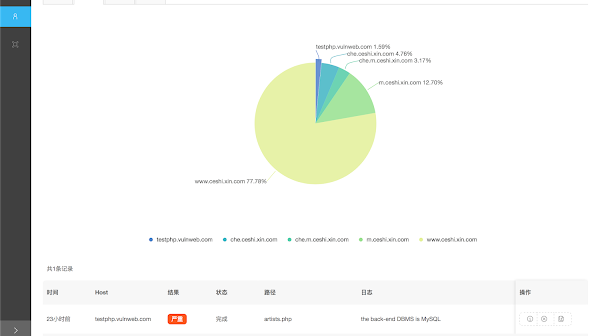
[sc name=”ad_1″] Automatic SQL injection with Charles and sqlmapapi Dependencies Django PostgreSQL Celery sqlmap redis Supported platforms Linux...
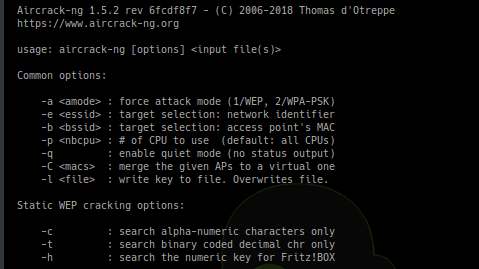
[sc name=”ad_1″] Aircrack-ng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security:...