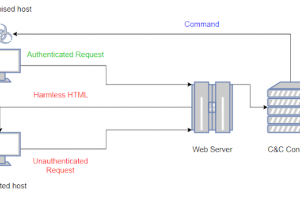
[sc name=”ad_1″] LOLBITS is a C2 framework that uses Microsoft’s Background Intelligent Transfer Service (BITS) to establish the...
Search Results For - Remote
[sc name=”ad_1″] What is “Kill Chain”? From Wikipedia: The term kill chain was originally used as a military concept related to the structure of an...
[sc name=”ad_1″] Did you ever wonder how you can move laterally through internal networks? or interact with remote machines without alerting EDRs...
[sc name=”ad_1″] SecGen creates vulnerable virtual machines, lab environments, and hacking challenges, so students can learn security penetration...
[sc name=”ad_1″] By @s0lst1c3 Disclaimer DropEngine (the “Software”) and associated documentation is provided “AS IS”. The Developer...
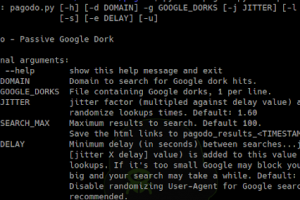
[sc name=”ad_1″] The goal of this project was to develop a passive Google dork script to collect potentially vulnerable web pages and applications...
[sc name=”ad_1″] Sinter is a 100% user-mode endpoint security agent for macOS 10.15 and above, written in Swift. Sinter uses the user-mode...
[sc name=”ad_1″] Many usefull offensive CSharp Projects wraped into Powershell for easy usage. Why? In my personal opinion offensive Powershell is...
[sc name=”ad_1″] A proof of concept crypto virus to spread user awareness about attacks and implications of ransomwares. Phirautee is written...
[sc name=”ad_1″] Bastillion is a web-based SSH console that centrally manages administrative access to systems. Web-based administration is...