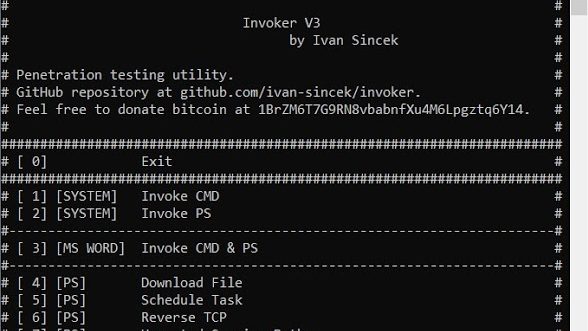
[sc name=”ad_1″] Penetration testing utility. The goal is to use this tool when access to some Windows OS features through GUI is restricted. Some...
Search Results For - Registry
[sc name=”ad_1″] UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting...
[sc name=”ad_1″] These files contain configuration for producing EDR (endpoint detection and response) data in addition to standard system logs...
[sc name=”ad_1″] A utility to analyze malicious JavaScript. Installation Simply install box-js from npm: npm install box-js --global Usage Looking...
[sc name=”ad_1″] This tool launches attack on k8s cluster from within. That means you already need to have an access with permission to deploy pods...
[sc name=”ad_1″] The Memory Process File System is an easy and convenient way of accessing physical memory as files a virtual file system. Easy...
[sc name=”ad_1″] Mondoo is infrastructure and security analytics your cloud-native applications. By removing the code literacy, we strive to make...
[sc name=”ad_1″] Cynet goes head-to-head with CrowdStrike, DarkTrace, Cylance, Carbon Black & Symantec, offering their unhappy customers a...
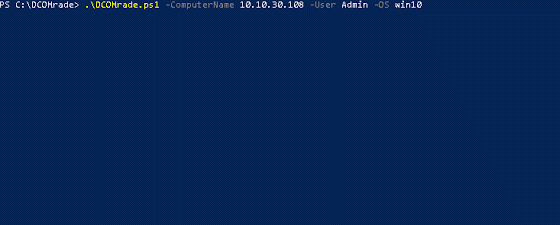
[sc name=”ad_1″] DCOMrade is a Powershell script that is able to enumerate the possible vulnerable DCOM applications that might allow for...
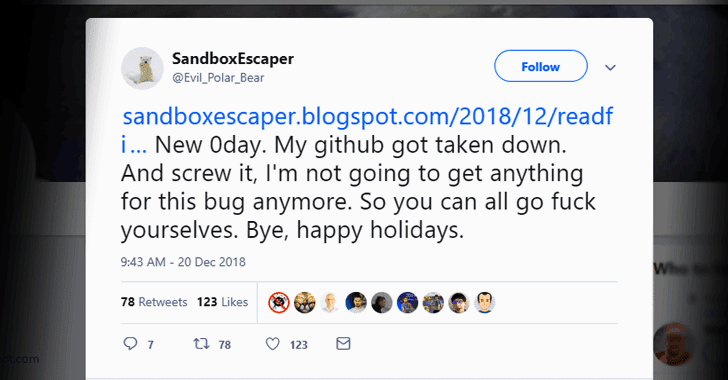
[sc name=”ad_1″] A security researcher with Twitter alias SandboxEscaper today released proof-of-concept (PoC) exploit for a new zero-day...