Author: Cole Gibson Before it became intertwined in the controversy surrounding Facebook’s misuse of data, Cambridge Analytica was planning to raise funds for...
Search Results For - Recon
Virtual Machine for Adversary Emulation and Threat Hunting RedHunt aims to be a one stop shop for all your threat emulation and threat hunting needs by...
CloudFrunt is a tool for identifying misconfigured CloudFront domains. CloudFront is a Content Delivery Network (CDN) provided by Amazon Web Services (AWS)...
With this tool you can block HTTP Flood Attacks and analyze them with a honeypot. THE TOOL SEND YOU AN ADVERTISING EMAIL AFTER DETECT A DDOS ATTACK! First...
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also...
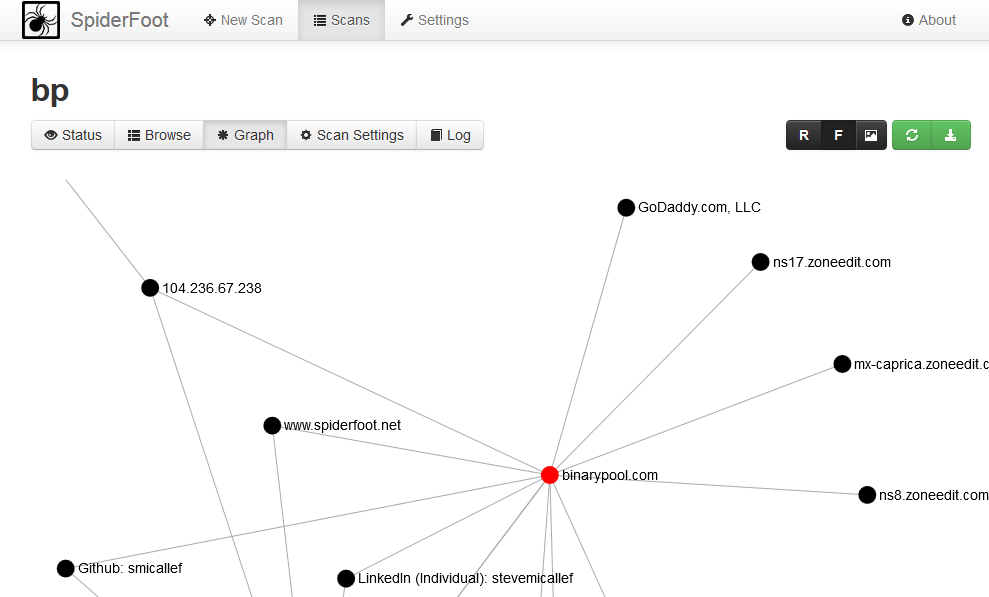
SpiderFoot is a reconnaissance tool that automatically queries over 100 public data sources (OSINT) to gather intelligence on IP addresses, domain names, e...
bettercap is the Swiss army knife for network attacks and monitoring. How to Install A precompiled version is available for each release, alternatively you can...
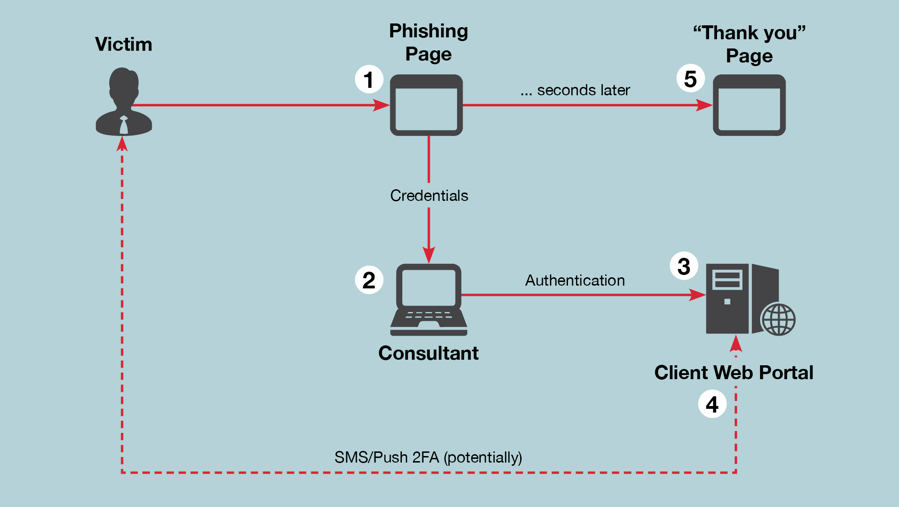
ReelPhish simplifies the real-time phishing technique. The primary component of the phishing tool is designed to be run on the attacker’s system. It consists...
The script will use msfvenom (metasploit) to generate shellcode in diferent formats ( c | python | ruby | dll | msi | hta-psh ) injects the shellcode generated...
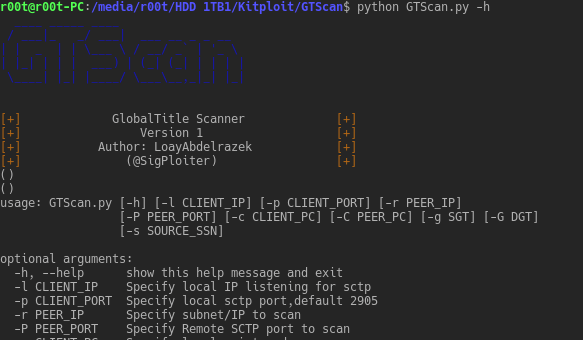
The Nmap Scanner for Telco. With the current focus on telecom security, there used tools in day to day IT side penetration testing should be extended to...