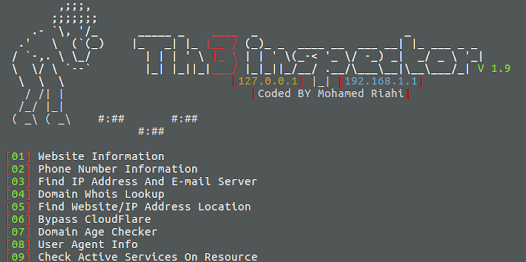
Tool For Information Gathering. Usage Short Form Long Form Description -i –info Website Information -n –number Phone Number Information -mx...
Search Results For - Protection
FIDO U2F Security key is a personal encryption method which individualizes your online security by providing a secondary layer of encryption via the USB port...
The Rogue Toolkit is an extensible toolkit aimed at providing penetration testers an easy-to-use platform to deploy software-defined Access Points (AP) for the...
The group, which embodies countless tech organizations including Google, Amazon, Facebook, Etsy and various companies, stated that the organization will not...
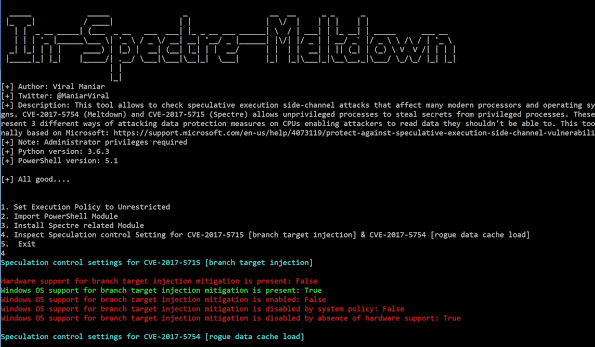
This tool allows to check speculative execution side-channel attacks that affect many modern processors and operating systems designs. CVE-2017-5754 (Meltdown)...
As the FCC has attempted to abandon its role as the defender of a free and open Internet at the federal level, states are attempting ways to step into the void...
The streaming company retweeted its care for the Internet Association’s Friday announced it would “interrupt in a judicial action to save net neutrality...
Defeating Google’s audio reCaptcha system with 85% accuracy. Inspiration Across the Internet, hundreds of thousands of sites rely on Google’s...
A security researcher (@s1guza) has published the details of an unpatched vulnerability in macOS that can be exploited to gain full control of a system. The...
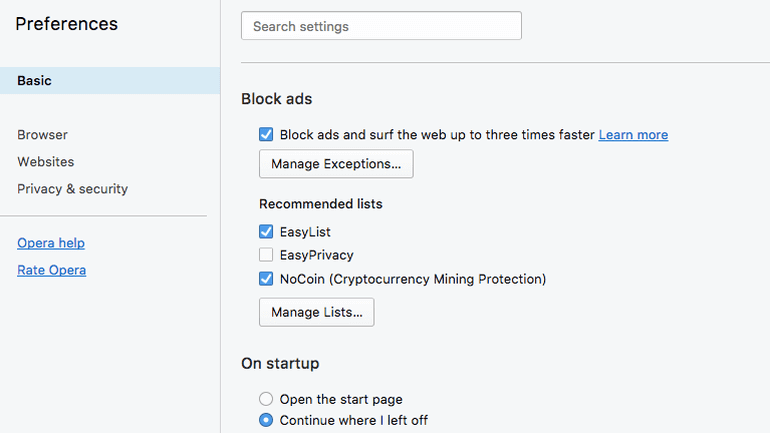
Norwegian browser maker Opera has launched the beta version of Opera 50, the first popular browser to integrate a built-in cryptocurrency-mining blocker. The...